What hides behind the phrase „the safest messenger for phones”? Many popular applications do not protect our data but rather spy on us, listening to our conversations or checking the messages we send. During tax proceedings or investigation processes, the law enforcement can take over the content of our conversations and messages. CBA (Central Anti-Corruption Bureau), CBŚ (Central Investigation Bureau) or police collect even the data saved on the SIM card. Wiretapping is necessary to fight organised crime. But it turns out that everybody is tapped – private individuals, entrepreneurs and politicians.
Last year, WhatsApp, a member of the Facebook family, transferred 1000 recorded conversations to the Polish law enforcement authorities. New York Times has reported that the experts from Check Point discovered a vulnerability in the application, allowing fraudsters to capture messages sent during group discussions or private conversations and manipulate their content.
The researchers claim the gap is substantial. Carl Woog, the spokesman of WhatsApp, claims that the Check Point’s discovery has nothing to do with a gap, because it doesn’t regard end-to-end encoding. And that is really the case – the experts’ discovery is not an unprecedented attack on protocol, but use of an already available text quoting function in the group chat that is susceptible to manipulation.
According to the findings, the „gap” allows for three types of attacks:
1. Modification of reply to attribute words to an author who did not really say them.
2. Quoting messages in reply within a group conversation to make it seem like it was sent by a person who is not even a member of the given group.
3. Sending a group member a message which seems to be a group message but is, in fact, sent only to this specific group member. The reply of the group member is, however, sent to all persons in the group.
WhatsApp encryption
It is a known fact that WhatsApp encrypts all messages, photos, calls, videos or other types of content we send. Using the Burp Suite program to analyse traffic between the application and the server, the researchers managed to decrypt WhatsApp communication and discovered that the protobuf2 protocol is used for communication encryption. Converting these data to Json allowed to see sent parameters and gain control over them.
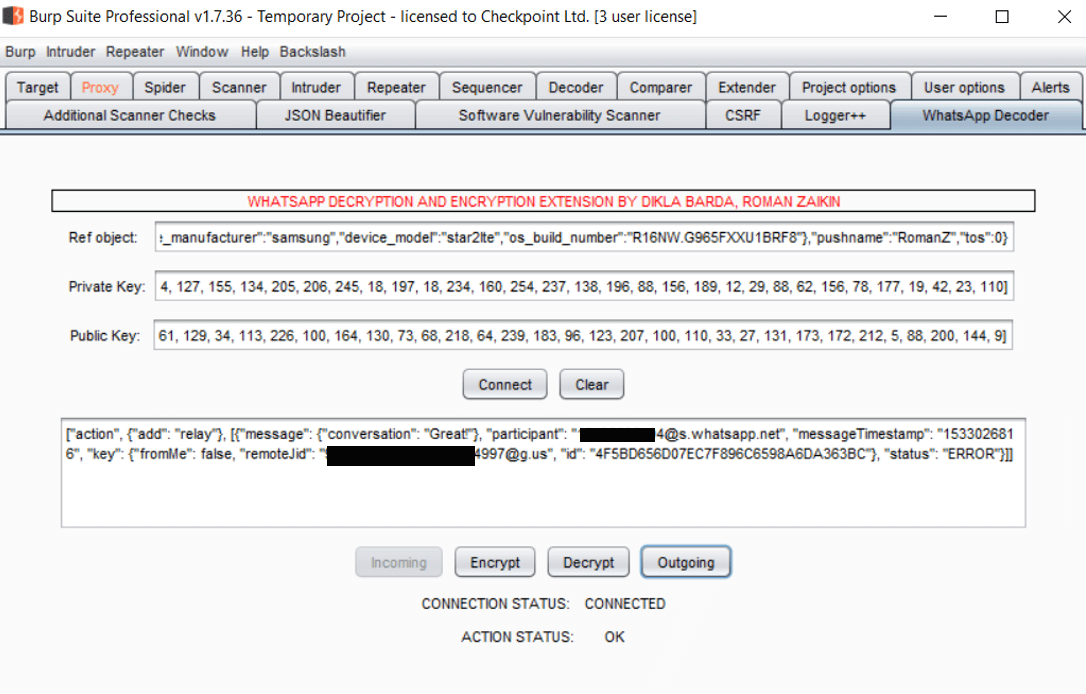
Therefore, at least one of the following conditions must be met for an attack to be successful:
- The fraudster can listen to the packets sent from the phone to the mobile telecommunication transmitter, i.e. use the so-called ma-in-the-middle attack by means of a device like this.
- The fraudster will do the exact same thing if he manages to plant his own wireless network.
- The fraudster must be on the group of chatting users.
To even start thinking about an attack, the fraudster needs special equipment and software. All the efforts of the criminals be in vain if the victim uses any VPN connection.
Therefore, what is the safest messenger?
Mk My Data presented such a benchmarking analysis in the report entitled „Technology in reins”. The name doesn’t ring a bell? It doesn’t for us either, but it specialises in data recovery from hard drives and mobile device memory. The following messengers were taken into consideration: WhatsApp, Signal, Facebook Messenger, Viber, Hangauts, Message and Usecrypt developed by a Polish company. It must be noted that there is a broad range of various types of mobile applications for correspondence exchange available on the market, but Mk My Data decided to focus on the messengers it encounters the most frequently when executing orders, preparing expert opinions or performing tasks connected with extraction of information from mobile devices.
The conclusions include the following statements:
As a priority, we recommend using the UseCrypt’s application guaranteeing the most secure and effective solutions. It can be definitely confirmed that there is no other such a comprehensively secure solution among the messengers currently available on the market.
The following messengers were taken into consideration in the experiment:
Signal
- It offers increased information exchange security level by means of end-to-end encryption.
- Unfortunately, messages can be separated from a stolen active device using available data acquisition methods.
- The data are kept on the servers of an American company – Open Whisper System, i.e. the developer of the messenger.
- The messenger is free and does not really grant access to knowledge what data and contents are collected on its servers.
- The con are quite unclear premises, coming to the light of the day from time to time, which bring up the question if there are some giant corporations or even special services behind the developers of this messenger (this theory is supported by multiple facts, for instance: the product is free and not advertised in any manner, even though development of such phenomena in the secure connection industry requires quite substantial investments and financial outlays).
- According to available information, the project is supported only from financial donations and subsidies.
- In the negotiation process, the Signal messenger uses the Diffie-Hellman protocol, with value 2 adopted as the generator for its multiplicative group modulo p. In reality, the generator of this group is number 5. As a result of application of the incorrect value, the protocol operates only on the subgroup of the indicated multiplicative group, thus significantly compromising security of the entire protocol and, in consequence, the communication process.
- Full encryption in group chats is active only if all users have updated software and the latest application version. Failure to update the software by even one member of the group makes the entire security and anonymity plan crumble.
- The WhatsApp conversation data are encrypted, but their metadata are not. This means that recipients, senders, connection dates, IP numbers, telephone numbers, pseudonyms, or the so-called nicks, as well as file sizes are available for the producer.
- The data are collected on Facebook servers. Correlating this information with the recent events or scandals involving Facebook, we can draw conclusions regarding safety of use of this application.
- Encryption in WhatsApp is also quite delusive as it does not protect against spying applications or keyloggers.
- WhatsApp features no authentication methods or means of confirmation whether the person we’re chatting with is really the person we intended to communicate with.
Viber
- It offers full encryption between users and relatively high security due to application of end-to-end encryption.
- It allows to confirm the identity of the chatting persons.
Imessege, Facebook Messenger and Hangouts
- They feature protection in the form of encryption and offer the same functionalities as described above.
- Their producers can obtain the content of correspondence from mobile devices on which they are installed.
- Physical possession of the user’s telephone or tablet, it is possible to access complete, full correspondence, including deleted elements. If such a device is obtained and copied physically, the entire correspondence of the device owner can be read.
Usecrypt Messenger
- This messenger is a visionary solution developed by Polish engineers.
- Connections in UseCrypt Messenger are configured through a proxy server which does not participate in any cryptographic operations. This guarantees full anonymity to the user. What is more, it is the only application allowing to check if the phone is under invigilation.
- The service provider does not store the user’s data on the server. In case of UseCrypt Messenger, when the user is registered, only cryptographic abbreviations are compared (obscured sequence from which it is impossible to recreate the telephone number). It is the so-called one-way function that allows to inform the user about his contact persons who use the service.
- The messenger offers an option to extend the safeguarding features by means of an application access code and the „PANIC CODE” function – useful especially in emergency situations. This function allows to erase all data regarding conversations, history of calls and list of contact persons from the device memory. This operation results in commencement of another client registration process.
- It uses a mechanism encrypting voice calls (the conversation encryption method is CBR).
- The protocol used in the UserCrypt Messenger ensures full end-to-end encryption. It also features a mechanism detecting man-in-the-middle attacks.
- AES encrypting algorithm is used for communication encryption.
- The product of the Polish company, Usecrypt S.A., allows for anonymisation of the network address of the service users.
Verification of the technical information supplied by the producers of all the messengers is very difficult. The subject of encryption and privacy must be approached very carefully and not favouring any of the available programs. Some applications considered safe could have now be tapped by services of certain countries. What is more, in the recent months we have seen that their producers are obliged under the law to transfer decrypting keys to the local authorities – lately, an American company – Continental – has banned the use of WhatsApp on company phones due to data security concerns.
Czy ten artykuł był pomocny?
Oceniono: 0 razy

