In October 2019, the CheckLab.pl organization prepared a summary of popular free applications to protect personal computers. So what is the best free antivirus? It is difficult to answer this question because a variety of free solutions makes the decision is not so obvious, additionally only big developers can offer relatively good protection. It is important to remember that free antivirus do not protect against all types of attacks. Free security software does not have the variety of functionality as commercial equivalents, so free antivirus should be at least complemented by a safe browser for online banking as well as a set of browser extensions to improve privacy and data protection.
Test of free antivirus has been performed by the CheckLab.pl organization which was founded in July 2019 by the AVLab.pl company which has been present in the industry of cybersecurity since 2012. The primary objective of the CheckLab organization is to test the usefulness of workstations security, issuing certificates confirming the protection effectiveness against malicious software, and also provide results to public information while ensuring the maximum transparency of the tests. The primary objective of the CheckLab organization is to test the usefulness of workstations security, issue certificates confirming the protection effectiveness against malicious software, and also provide results to public information while ensuring the maximum transparency of the tests. In the tests, the CheckLab employees use malicious software, tools, and techniques of bypassing security that are used in real cyberattacks.
The comparison of free antivirus aims at providing the current situation of each products on the market in terms of detecting and blocking threats extracted from Internet:
- Recommended free antivirus from AVLab
- Recommended the best specialized security suites from AVLab
Comparison of free and paid antivirus — what are the differences?
The decision on the choice of antimalware solution depends on many factors. If we consider free security software that is, for example, Windows Defender which has the advantage of being ready to use straight out of the box. It does not require any configuration. It just provides a basic protection from the first seconds.
The disadvantage of a free solution in the case at hand is the technical limitation because Windows Defender protects only the Windows system. That is why it is worth to make use of external plugins for popular browsers. Another argument in favor of the limited security of Microsoft is the SmartScreen function that makes it easier to indentify phishing websites containing malicious software, and make informed decisions concerning downloading files. Smart Screen works only with the Microsoft EDGE and archaic browsers of the family Internet Explorer. Users of the Chrome or Firefox browsers have to make use of external plugins if they want to keep free protection which does not serve people with insufficient knowledge of security and cyber threats.
Today’s complete security solutions go far beyond a basic protection, so Windows Defender works well as elementary security which as of today cannot compete with big developers. Microsoft is focused on the protection of the Windows ecosystem. In some tests the native solution of Windows Defender is less effective than competitive software. In addition, Microsoft does not complements its offer by a comprehensive security of mobile operating systems or managing protected devices from one central point. Family functions are available in the Windows system that help monitor online activities of a child, but still lack the option of managing parental control that would cover few devices.
External developers of security solutions provide functions of remote access, cloud management, file encryption, parental control, setting up VPN connections, scanning IoT devices connected to home network, and much more. So far, Microsoft offers only antimalware solution. Restricting Microsoft to one operating system has led to a situation where the Windows Defender solution is hard to compete with the biggest developers from the industry in terms of the complexity of protection and security of various operating systems.
What is missing in free products?
The AVLab.pl portal and the CheckLab.pl organization, obliged to raise awareness and educate, have to take responsibility for published tests and comparison. Practice shows that a large number of people is unaware of cyber threats. Low awareness extends to the lack of a basic knowledge of pros and cons solutions available on the market. There are so many products that even psychological studies confirm — the more a user has to choose, the more difficult to make the right decision. Each developer presents to end user its own marketing data, and multiplying these information by amount of suppliers, it is not easy to get through such an unimaginable portion of information. The amount of data in the context of the whole security market can be overwhelming even for experts who find it hard to keep up with products that dynamically evolve. As a result, unaware users instead of ensuring at least a basic protection, they do not go for any of the available.
What is missing in free antivirus products? We will describe specific situations, why free solutions cannot compete with paid equivalents. It really comes down to the fact that free applications are usually versions that are indented to provide only basic, demonstration protection. They generally lack:
Additional protection in a browser
This trend slowly changes, but we can even now think of free products that do not scan websites or downloaded files before those are saved on a computer’s hard drive. The solution mentioned above, Windows Defender provides protection only in the EDGE browser. There are security issues that have been provided for in products with comprehensive security, waiting for users unaware of threats.
Online banking protection
In early 2017, the AVLab.pl organization performed the test to prove if so-called “safe browsers” or “virtual environments” that isolates sensitive processes of the Windows operating system, are actually suitable for what they have been programmed for. Detailed information can be found in the report “Test of software for online banking protection”.
Free solutions does not usually have such protection. If we do not isolate a financial environment from an operating system, the risk of loss of money is increasing. Having an online banking protection installed on a computer, a user has grounds for believing that he is well protected against manipulating of data input at the level of a browser interface. But that is not all, during browsing HTTPS websites, an attacker who has taken control of a system, is not able to inject malicious DDLs into processes of “safe browser”. He is also unable to perform MiTM attacks within the range of WiFi network, or inject false SSL certificates without warning message of antivirus (if attacker managed to do this, he could decrypt packets passing through the HTTP protocol, modify, and encrypt them again by sending manipulated data to a browser).
Firewall
In 2017, there was a global epidemic of malware. The WannaCry ransomware were spreading to other computers through files transfer by vulnerable SMB protocol in the first version. All Windows versions are vulnerable to this attack when they do not contain updates published in the MS-17-010 bulletin. And the MS-17-010 bulletin was published in March 2017, and it contains updates for Windows 10, Windows 8.1, Windows 7, Windows Vista, Windows Server 2016, Windows Server 2012, Windows Server 2008, and the Embedded version. The scale of spreading the WannaCry ransomware has turned out to be so great that Microsoft has released the update for already unsupported Windows 8, Windows XP, Windows Server 2003, and Embedded equivalents.
A two-way firewall should protect against these kind of network attacks containing Intrusive Detection System (IDS) that detects attacks of ARP poisoning, DNS modification, PING false positives, exploiting SMB, RPC, RDP protocols, and port scanning. Firewalls were designed to prevent attacks on the part of those who have bad intentions. Attacks overloads network, could be a problem for many companies or individuals. An effective firewall should be flexible in terms of configuration. It must adjust to user needs, recognize independently operating mode (e.g. during a game). It should be suspicious for unknown processes to prevent intrusions, even if malicious software is not yet analyzed by other protection components. A good firewall acts as a preventive security. The Windows system has considerable deficiencies in this regard because an embedded firewall differs significantly from the IPS/IDS systems.
Parental control
This kind of modules are use for parents because they allow to control access to unwanted content for children, block incoming calls and text messages from unknown numbers on mobile devices, and also tracking phone through the GPS or WiFi modules. Parents should be informed about inappropriate actions via email so they can respond quickly.
Advanced protection against ransomware
Ransomware is spread mainly via spam that contains malicious links and attachments. Free solutions do not have protection of protocols that support email through email client. It is worth to use security software that includes the protection against different vectors of attacks: email, websites, network communication, peripheral devices.
First seconds are the most important after opening a fake invoice or notified parcel. That is when ransomware begins to search and encrypt files — most often with the AES-256 or AES-128-CBC algorithms. Next, private and public keys are generated on a server controlled by an attacker (mostly with the RSA-2048 algorithm or stronger). Such a public key is downloaded on a victim’s computer. Using a public key, ransomware encrypts a previous AES-256 key through which documents, movies, databases, computer games files are encrypted. In cryptography, large prime numbers give an advantage to criminals. Subject of prime numbers and their problem is perfectly shown in the movie „Przekleństwo liczb pierwszych. Hipoteza Riemanna”. Modern computers are powerless against cryptographic attacks that is why using appropriate security will allow to protect folders from encryption.
Anti-stealth module
Useless until first loss or theft of a device. Smartphone or laptop monitored by software built into security solution can be localized or blocked. Antivirus product can shoot photos of new “owner” by accessing a webcam. Police will also find useful IP addresses by means of which a device has recently connected to the Internet.
Scanner of running commands in Windows
“Fileless” type malicious software operates directly in computer’s memory. In such a scenario, running virus will not be quarantined by security software because it is not a file but a set of instruction to perform which operates in system processes.
A while ago, experts from Kaspersky have detected a series of “invisible” targeted cyberattacks. Malicious software has not been downloading any harmful files on a hard drive, but it was hiding inside memory. This combined approach helps avoid detection by whitelist technologies, and does not almost any traces or malware samples to people conducting forensic examinations which they might work with. Attackers remain in a system long enough to collect information, after which their traces are erased with the first reboot of a computer.
Then, it was found out that authors of the attacks have used legitimate PowerShell scripts and other tools which were adapted for a harmful code that can hide inside memory secretly gathering passwords of system administrators in order to allow an attacker to take remote control over victim’s systems. The ultimate goal of cyber criminals seems to be an access to financial processes.
An infection vector most often starts traditionally that is after placing malicious file on victim’s computer through scam or drive-by download attack using exploit that is why it is again worth to rely on a comprehensive protection of many protocols.
Authors of malicious code who are often experts in their field make use of mechanisms not to leave any traces on a hard drive, and make it difficult to detect a virus by a protection application. Security software which have firewall and IPS (Intrusive Prevention System) modules scans outgoing and incoming traffic established by system processes, making them privileged for products that provide only a basic antivirus protection.
“Fileless” threats have several common traits with rootkits: can store data in the registry which is a database for settings of operating system and some applications, or even capture and modify low-level API functions. In addition, like rootkits, they can cover up the presence of individual processes, folders, files, and registry keys, including an installation of own drivers and services in a system. Fileless malicious software can access system privileges. A process launched at this level (ring-0) executes code with system’s core privileges. As a result it can get unlimited access to all processes, driver, and services.
Encrypted VPN tunnel
By connecting with a bank through banking application or logging into a server through SSH, it is always worth to activate VPN. Not to be anonymous because it is not designed for this, but to secure a communication channel with an additional encryption layer. It is important on smartphones because the whole network layer is encrypted, so the whole traffic, and not only browser queries (like e.g. in free VPN built into the Opera browser).
A mobile device is the most exposed to attacks in public places even with secured hotspots. KRACK is a compulsory subject for all who use WiFi in different places. There are many vulnerabilities in the WP2 protocol, although some devices can contain more than one vulnerability. However, before you start to log into wireless networks in flats, college, at school, or work, make sure that routers and access points have installed security patches. How to do it? This knowledge is reserved for technical users (you can use a simple script running in the Python interpreter that verifies if nearby access points are vulnerable to KRACK):
[15:48:47] AP transmitted data using IV=5 (seq=4) [15:48:47] AP transmitted data using IV=5 (seq=4) [15:48:47] IV reuse detected (IV=5, seq=4). AP is vulnerable!
However, who will want to verify every access point? Even advanced maniacs does not do that. Since, in practice it is hard to verify if any access point is vulnerable to KRACK, it is better to avoid public (and even secured) WiFi networks. It is simply safer to use mobile network provider, i.e. mobile Internet. Or use VPN.
This matter is so serious that largely ignored security policies can lead to decrypt all communications between a device, access point, and server. Also remember that protocols which use encryption, like HTTPS, SFTP, SMTP, IMAP, and others, are immune to eavesdropping. It is worth to use VPNs that create sort of special tunnel between a device, and server. By encrypting all communications, VPNs provide complete immunity to KRACK even on unencrypted websites.
Home network monitor
“Home network monitor” in the context of vulnerability of routers will help to indicate weaknesses in home network security, but not only. In public places, it will check if a password to a router is strong enough, identify devices connected to a router, and very important provide a user with insights into unknown devices nearby. Then, you might want to be careful and break a connection with such a network, or connect to the Internet using VPN mentioned above. In addition, “Home network monitor” will indicate gateway address, so IP address of an access point by which devices in a local network communicate with the Internet, and less technical users to whom this module is addressed will get a research on devices located near an access point.
Checking updates of applications and system
Attacks are effective because they exploit vulnerabilities in software. Therefore, you need to make sure that an operating system has security updates. Such modules detect and inform about not installed security updates, they recommend to install a new version of applications (among others, browsers, media players, and graphic viewers), and also propose to change passwords of a router and system, if they turn out to be too easy to guess.
Optimization module
Such modules cleans the Windows system from unnecessary temporary file. Remnants of installers, browser cookies, or even Windows Update files. Sometimes optimization includes insight into running applications at system startup, and it is possible to turn them off as well as an overview of the largest files on a hard drive that antivirus will quickly locate and delete if user decides to do so.
Storing and generating passwords
We do not need to encourage anyone to conveniently store passwords hard to remember. Today, you should use unique credentials on every website. Passwords managers are here to help not only remember, but also generate a password difficult to crack. Besides, secure passwords are only the basis of online account protection. Now, you have to use a multi-component logging not to be a victim of an account theft, e.g. to Facebook, as in the case described by us.
Files encryption
Files encryption protects data from falling into the wrong hands. A created contained can be blocked at any time. Every time computer boots, a user may be required to enter a password to a container (for safety reasons). A strong password to tray with files can be generated in a password manager, and store it there securely. Files encryption is effective in the current data protection directive. So called RODO applies to all, who are even self-employed. Encryption modules will also come in handy if we want to sell hard drive. It is worth to encrypt data in advance, because the last research of the Comparitech company shows that almost 60% used hard drives store data remnants of previous owners (among others passports scans, driver licenses, bank records, tax documents, visa applications, and even intimate photos).
Webcam protection
Monitoring an application access to webcams is an important function caring about privacy. Malicious software or hardware backdoor may access a webcam.
What if it was true?
Other features of good software
Individual users rarely make a backup of data. Their knowledge related to security is insufficient which affects their lack of awareness in the context of manipulation from authors of socio-technical attacks. A big threat lies in wait from not updated software, making it easier to attack with the use of exploits. Users are wrongly established in the belief that since they do not click on inappropriate links and visit suspicious websites, they have nothing to worry about. They are unaware that transparent drive-by download attacks exploit 0-day vulnerabilities in a browser and do not appear in any form. The only way to expose is when, e.g. a browser freezes.
Too often we can read comments “I do not have antivirus, why do I need antivirus. I do not visit porn websites. Windows Defender is good enough for me”. In the meantime, websites with pornographic content are no longer the main culprits responsible for infections. Comprehensive software that secures computers do not guarantee complete safety, but they are much better protected because they cover up much more Internet protocols.
Explanation of the “Advanced In The Wild Malware Test”
The name of the „Advanced In The Wild Malware Test” perfectly reflects its character. The source of malicious software are honeypots located on all continents of the world. We collect malware, among other, for the Windows system. Samples captured in attacks are checked on the basis of over 100 patterns before they are qualified for testing. These patterns allow us to determine whether a potentially dangerous file is actually a threat to the Windows 10 Pro operating system.
In October 2019, in the third edition of security tests of the „Advanced In The Wild Malware Test” we verified the effectiveness of detecting and blocking malicious software of 9 solutions for protecting computers.
The tests lasted continuously the whole October 2019. The list of tested solutions is as follows:
- AVAST Free Antivirus
- AVIRA Free Antivirus
- BITDEFENDER Antivirus Free
- COMODO Cloud Antivirus
- KASPERSKY Free
- NANO Antivirus
- PANDA Dome
- SECUREAPLUS Lite
- WINDOWS Defender
The results of October 2019
CheckLab as the first organization in the word shows such detailed information from tests to all interested people. We share checksums of malicious software by dividing them into protection technologies that have contributed to detect and stop a threat. According to experts, this type of innovative approach of comparing security will contribute to better understanding of differences between available products for consumers and enterprises.
A chart describing differences between individual products is available at http://checklab.pl/en/recent-results
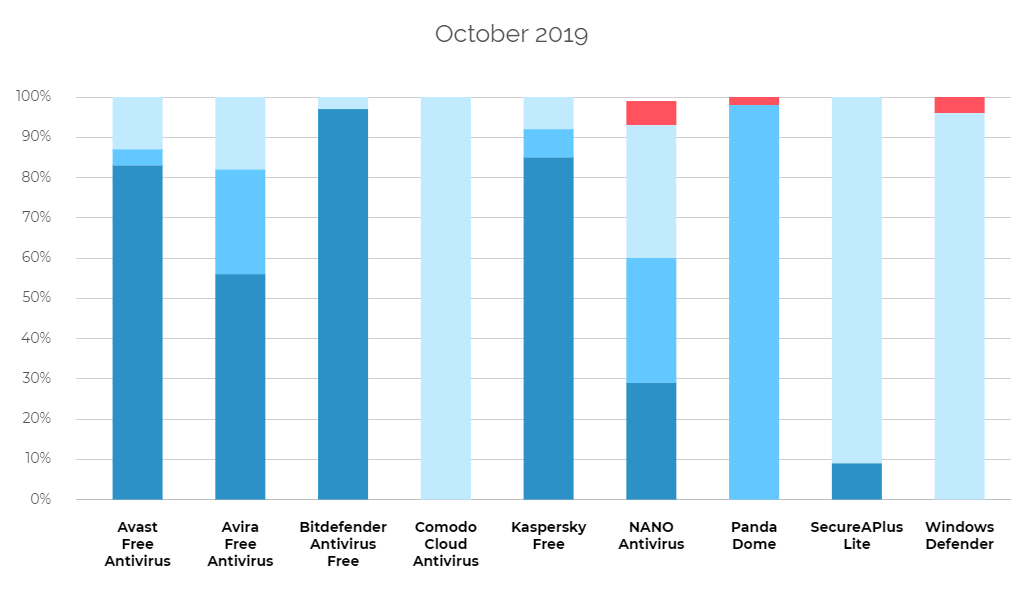
In the third edition of the test, we have granted the BEST+++ certificate to:
- AVAST Free Antivirus
- AVIRA Free Antivirus
- BITDEFENDER Antivirus Free
- COMODO Cloud Antivirus
- KASPERSKY Free
- SECUREAPLUS Lite
We have granted the BEST++ certificate to:
- PANDA Dome
- WINDOWS Defender
We have granted the GOOD+ certificate to:
- NANO Antivirus
Levels of blocking malicious software samples
The CheckLab employees are probably pioneers in this regard — they show more detailed diagnostic data than any other testing institution, including the largest such as AV-Comparatives and AV-Test. Blocking of each malware sample by tested protection solution has been divided into a few levels:
- Level 1 (P1): The browser level, i.e. a virus has been stopped before or after it has been downloaded onto a hard drive.
- Level 2 (P2): The system level, i.e. a virus has been downloaded, but it has not been allowed to run.
- Level 3 (P3): The analysis level, i.e. a virus has been run and blocked by a tested product.
- Failure (N): The failure, i.e. a virus has not been blocked and it has infected a system.
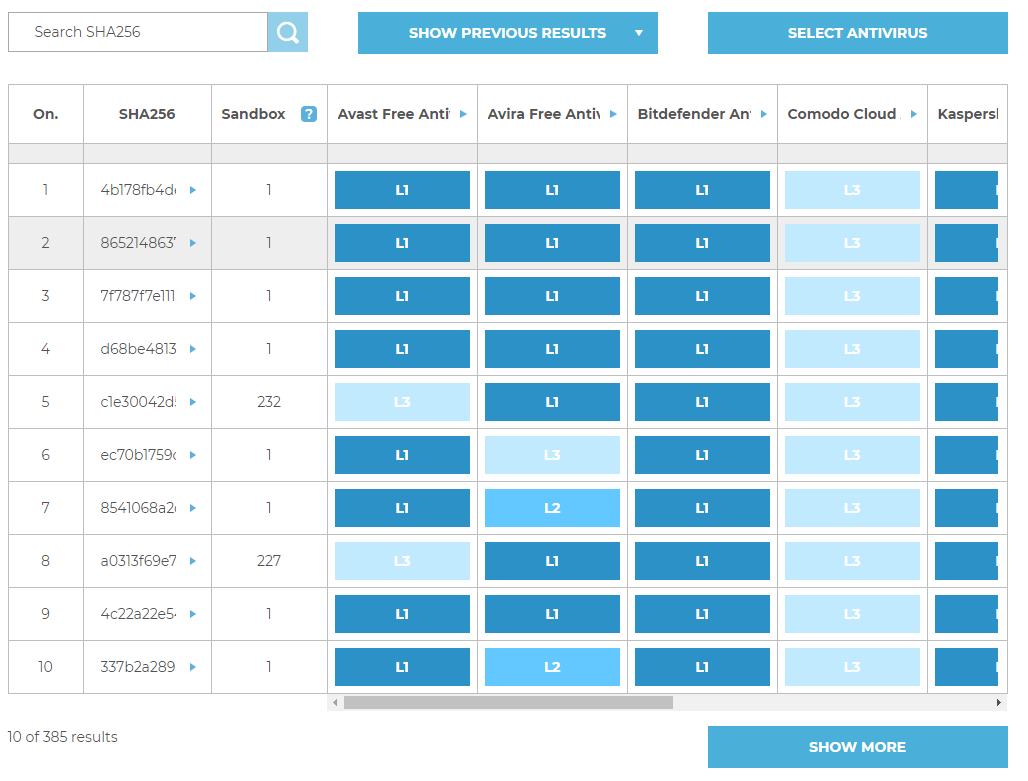
The results of blocking each sample are available at http://checklab.pl/en/recent-results in the table:
The products and Windows 10 settings: daily test cycle
Tests are carried out in Windows 10 Pro x64. The user account control (UAC) is disabled because the purpose of the tests is to check the protection effectiveness of a product against malware and not a reaction of the testing system to Windows messages.
Additionally, the Windows 10 system contains installed the following software: office suite, document browser, email client, and other tools and files that give the impression of a normal working environment.
Automatic updates of the Windows 10 system are disabled in a given month of the tests. Due to the complicated process and the possibility of a malfunction, Windows 10 is updated every few weeks under close supervision.
Security products are updated one time within a day. Before tests are run, virus databases and protection product files are updated. This means that the latest versions of protection products are tested every day.
Malicious software
We have used 385 malicious software samples for the test, consisting of, among others, banking trojans, ransomware, backdoors, downloaders, and macro viruses. In the contrast to the well-known institutions that verify the security usefulness, the CheckLab tests are much more transparent because the organization share the full list of malware samples.
During testing, all solutions have access to the Internet. The experts of CheckLab use real working environments in a graphic mode that is why the results of individual samples may differ from those presented by the VirusTotal service. The CheckLab organization points that out because inquisitive users may compare our tests with the scanning results of VirusTotal. It turns out that differences between real products installed on Windows 10 and scanning engines on VirusTotal are significant. We have explained these discrepancies in the article “How we test antivirus? The making of CheckLab.pl, a website dedicated to security tests”.
Czy ten artykuł był pomocny?
Oceniono: 0 razy





