A few weeks ago, we took a close look at the Polish UseCrypt Messenger, which in many ways turned out to be better than Signal, Facebook Messenger, Telegram, and Viber. We would be hypocrites if we did not describe in detail the weaknesses and strengths of the product of Polish engineers’ work. As UseCrypt Messenger has many more strengths than weaknesses, there is little wonder it was the winner in our comparison. We do not want to copy the review of the messaging application as all you need to know about UseCrypt Messenger can be found on the AVLab website in this article Let us not go too far from cryptography and encryption because the information provided in the review of the messaging application can help understand this article. This time, we analyzed the UseCrypt Safe application developed by the company UseCrypt S.A.
All data stored in a cloud can usually be synchronized on many computers, but encryption is not always offered as an option. The UseCrypt Safe application adds this missing element. The need for encryption may be due to a fashion or another trend (as demonstrated by an example related to the blockchain technology, where an American tea maker Long Island Iced Tea changed its name to Long Blockchain and, as a result, the price of its shares increased by nearly 500%). UseCrypt is not changing its name and is not using the blockchain technology but addressed the need to guarantee legal security, e.g. for persons who sign NDA documents. In short, the UseCrypt Safe is perfect for those who want to securely store and share files and important documents and who want to ensure restriction of access to sensitive information to authorized persons. All these are features of the software, which is available in the cloud model. On the other hand, companies that treat privacy as a priority (privacy-by-design) can install all components needed for secure file sharing on the company network.
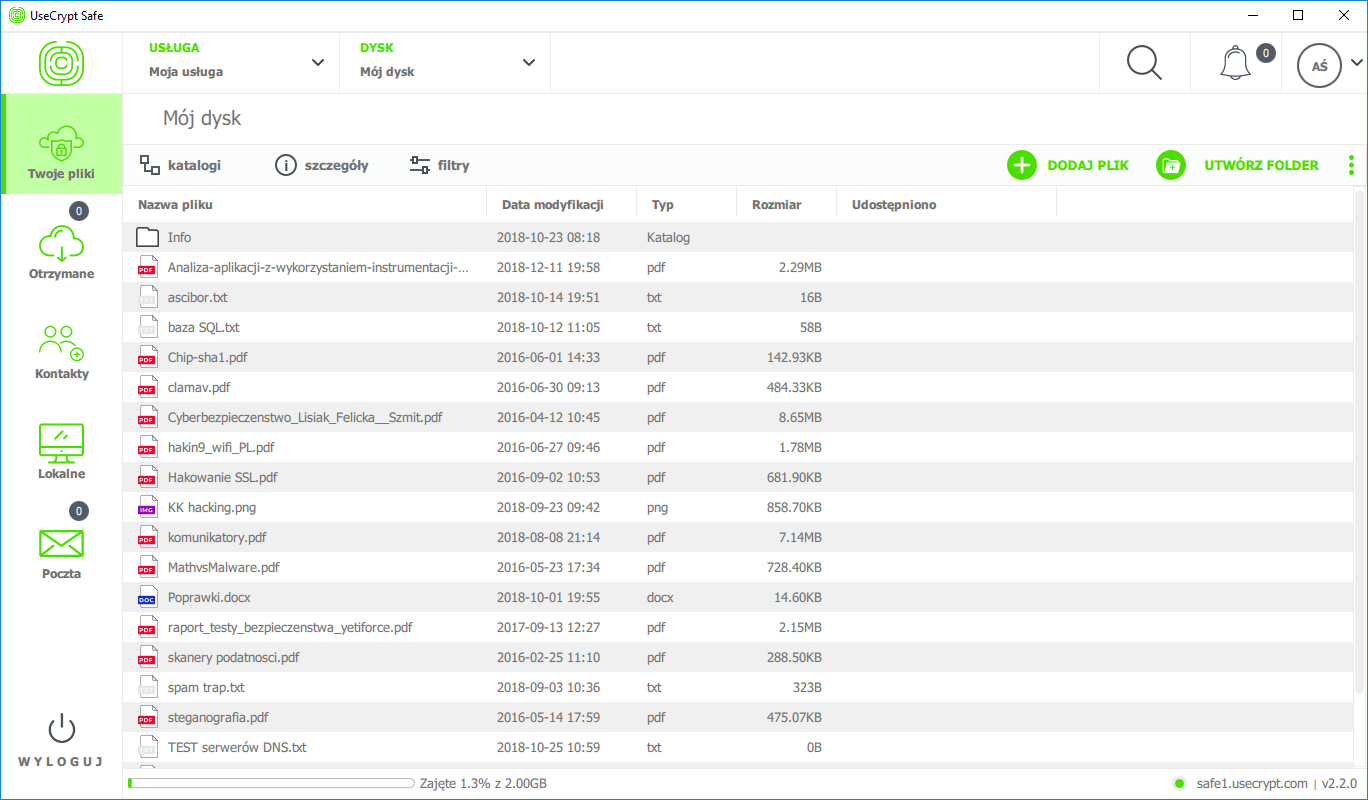
UseCrypt Safe appears to guarantee the same things that the common cloud data processing technology. This means that there is no need to worry about the hardware and that security and data backup are ensured by the service provider. However, after longer use of the application, one can reach the conclusion that UseCrypt Safe is more than a secure fire sharing service. In fact, the application makes the data NON-DECRYPTABLE even for the software developer company. UseCrypt S.A. is unable to decrypt the files stored on hard drives in its clouds, even if it wanted to. More demanding customers can find out by themselves. UseCrypt Safe can be implemented in the company infrastructure and, as the administrator, the company can have access to the backend server. The customer can see that there is no information or cryptographic keys stored there that would make it possible for the customer or the UseCrypt company to decrypt the files.
Encryption is not a common feature of cloud services. For example, such popular cloud services as Google Drive, Dropbox, or OneDrive, do not provide this functionality. Users of data storage services on Google or Microsoft servers must take care of privacy and security themselves – or they can use the UseCrypt Safe application.
UseCrypt Safe in a cloud vs. in private infrastructure
UseCrypt Safe in the 30-day free test version makes it possible to store files with total size of 2 GB. This is not much but enough to get familiar with the software. Private and company subscription costs 65 zlotys a month per user. The application can be installed on three devices with Windows and MacOS operating systems. The price per user is lower in packages of more than 25 licenses. By buying the subscription, one can increase the storage space from 2 GB to 100 GB, but it is also possible to buy additional 1 TB of storage space and to divide it in any way among all employees. The only shortcoming is the lack of applications for mobile systems. As we have found out, they will not be offered any time soon. Currently, the company focuses on users of desktop and laptop computers.
The table below shows a comparison of the standard version and the version of UseCrypt Safe installed on company servers.
| Function | UseCrypt Safe in a cloud | UseCrypt Safe on-premise |
|---|---|---|
| Storage of encrypted files | In the software maker’s cloud | On the customer’s servers |
| Encryption type | ½ na lokalnym komputerze i ½ w chmurze producenta | ½ na lokalnym komputerze i ½ na serwerze Twojej firmy |
| Rodzaj szyfrowania | HVKM + end-to-end + UST + AES + RSA + KDF + DH + MAC + KEM | HVKM + end-to-end + UST + AES + RSA + KDF + DH + MAC + KEM |
| Available space | Max. 100 GB and a multiple of 1 TB as an additional option. Moreover, it is possible to assign space for each employee, e.g. 25 GB. | The amount of space is limited by the drive space available. Also, limited space can be assigned to each user. |
| File encryption | On a computer with the application installed | On a computer with the application installed |
| Unlimited data transfer | YES | YES |
| Assistance | 24/7 assis tance | Pomoc 24/7 |
| User management | NO | YES |
| Supported systems | Windows, macOS | Windows, macOS |
| Availability (SLA) | 99,9% | Depending on your company |
| Additional costs | NONE | Provision of machines and employees responsible for infrastructure maintenance |
Data can be shared in the safest manner in groups established with co-workers, the management board, the directors, or people who simply do not want to anyone to be able to read their emails and attachments. Emails and attachments can be read, for example, by algorithms that analyze emails and that share information with advertising companies (or law enforcement agencies) as well as by the email server administrator.
Access to an email server does not mean that someone is using the data stored on it. This does not change the fact that such use is possible, because it is technically possible. Moreover, it is very tempting to do so. So much so that technological giants do collect additional information about customers and use it as an additional income source. Forced data sharing – is this the price of free services? It must always be assumed that a free mail GMail or Outlook account is offered in exchange for the information contained in the messages, including the contact list. Companies such as Google, Microsoft, Yahoo, WP, Onet, Interia, and Facebook collect their users’ data and often provide it to their partners and advertisers. It is true that users are provided with various terms and conditions and data processing consents but their content can only be fully understood by a lawyer (or should be analyzed using the https://bringingprivacyback.com website). No sane person would agree to share information with advertisement providers, such as Google and its partners (advertising and marketing experts) do. Access to information collected by customers using the service is often not transparent. Millions of users have discovered that.
Private mail is not private. Google treats its users as a commodity.
A few years ago, Wall Street Journal journalists got information that demonstrates that Google does not respect the privacy of GMail users. Using their GMail address, users would register for other services that would receive the permission to access the contents of the users’ mailboxes. One of the suspect companies is Return Path Inc. which collects data for advertisers by scanning inboxes of over two million people who have registered for one of the free applications of Return Path through their Gmail account or their Outlook or Yahoo accounts. Computers used for machine learning usually scanned about 100 million emails a day! After a while, „machine reading” was not enough and the employees of Return Path had to read about 8,000 emails in order to better teach the algorithms analytics. Return Path Inc. refused to comment this topic but it stated that sometimes they allow their employees read emails when solving problems with algorithms.
In a similar case, employees of Edison Software, which is developing an organizer application, read themselves electronic mail of hundreds of users in order to create a new function, said Mikael Berner, the General Manager of the company.
Allowing third-party companies to read email messages has become a common practice. Thede Loder, a former technology specialist at eDataSource Inc., stated that data of this type have occasionally been checked by his employees who read email messages while building and improving software algorithms.
Google has fought against privacy problems ever since it started GMail in 2004. Internal Google algorithms scanned messages and the company sold advertising space to interested partners. As many as 31 consumer and privacy protection organizations have sent a letter to Google’s founders Larry Page and Sergey Brin in which they stated that this practice raises huge concern and affects the trust in the email service supplier. Google stated bluntly that displaying advertisements helped it compensate the costs of the free service and that the company provided data only to third party companies that had been verified based on some criteria. As the criteria are not known, this answer was not satisfactory.
In the years 2010-2016, Google was accused of violating American federal wiretapping regulations at least three times. In its defense, the company stated that its privacy policy expressly addresses provision of information:
We may share non-personally identifiable information publicly and with our partners — like publishers, advertisers, developers, or rights holders. For example, we share information publicly to show trends about the general use of our services. We also allow specific partners to collect information from your browser or device for advertising and measurement purposes using their own cookies or similar technologies.
Users are required to go to the Security Check-up website and check which applications connected to the Google account.
On 22 January 2019, Google intends to update its privacy policy for users from the European Union. Unfortunately, the updated policy still contains provisions about reading of the content of email accounts:
Our automatic systems analyze content (including of email messages) in order to offer personal service functions, such as search results, customized advertisements, and detection of spam and malware. We conduct such analysis at the time of sending, receiving, and saving of content.
Almost every developer of any application can develop software that will connect to Google accounts using an API. Companies that develop applications do not always have bad intentions. For example, the API makes it possible to use email in the Outlook or Thunderbird client. However, in other cases, malicious applications can display a button with a request for permission to access the inbox and to pretend to be legal software, being in fact a trojan. The API interface is provided not only by Google but also by Microsoft and Apple. This is a normal thing. Unfortunately, the API is not always used in a legal manner. The end users cannot do anything about it.
Users are also a commodity for Facebook
Facebook has for years allowed third-party companies to gain access to user data, e.g. by way of rights in applications. This practice was a cause of a scandal when, in 2018, Facebook announced that it suspected one of its partners of selling data about tens of millions of users to an analytical company that supposedly had links to Donald Trump’s presidential campaign in 2016. This leak has resulted in a review of the laws protecting the rights of users in the USA and in Europe.
Cambridge Analytica. Everything started in 2010 when Facebook provided the API interface to the Open Graph technology that even today enables adding posts and videos marked with tags. In 2011, Facebook signed an agreement with the US government and was allowed to provide personal data to third companies. If it breaches the agreement, it will be required to pay 40,000 dollars a day per user, which would result in Facebook’s bankruptcy and losses to its shareholders. Cambridge Analytica was established in 2013 in the UK and currently continues to operate in the USA. In the same year, Aleksandr Kogan, a Cambridge University professor designed an application that he used in his research. A year later, he established the GSR company that collected data and sold it to Cambridge Analytica.
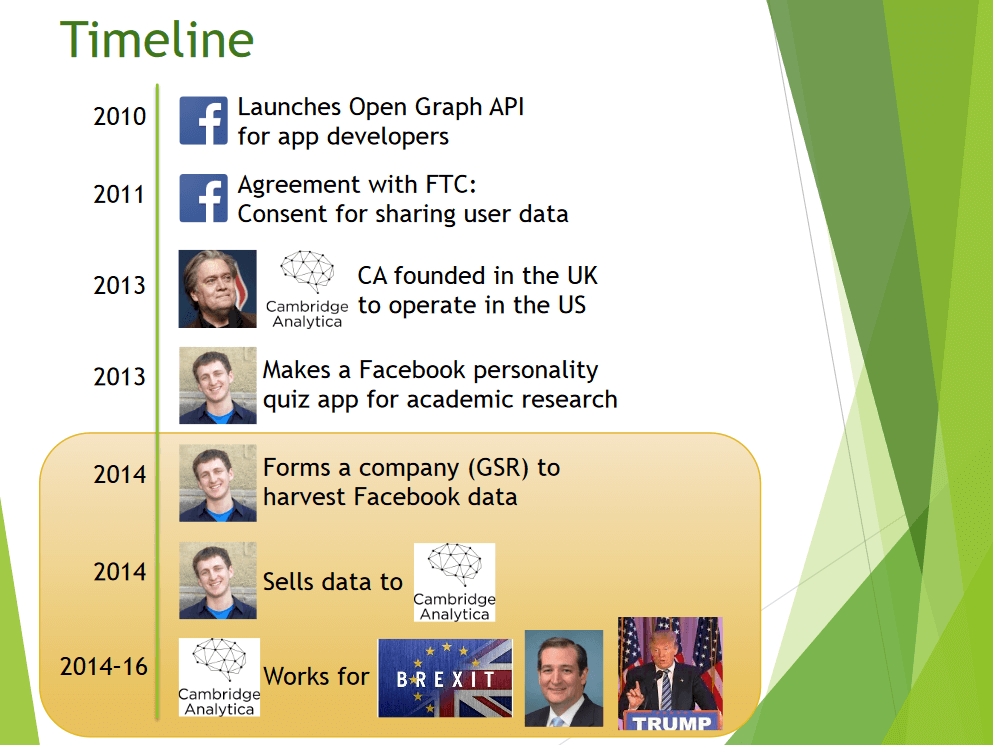
The rest of the history of Facebook and Cambridge Analytica is known. The social network was used to collect detailed data about American citizens. This was intended to help in the election campaign because Donald Trump’s campaign supposedly worked with Cambridge Analytica and obtained more accurate data on political preferences, shopping history, travel routes, financial documents, and personal communication.
UseCrypt Safe. File encryption and sending encrypted emails
Examples of spying and reading of messages can either drive people crazy or open their eyes. There is no such thing as a free lunch, so what benefits do Google, Facebook, Apple, and Microsoft get from providing free services? It is time to stop it, or at least to make it harder.
Privacy protection requires a broader approach. What choice do companies that do not want to disclose confidential documents to the public have? Encryption using the PGP protocol is safe but cannot be used in work groups. Luckily, in the march toward privacy, a Polish company with its UseCrypt Safe software is in the leading position.
UseCrypt Safe makes it possible to safely store encrypted and non-encrypted files, both locally or in a cloud. Users are authenticated with passwords that they use to log into the application.

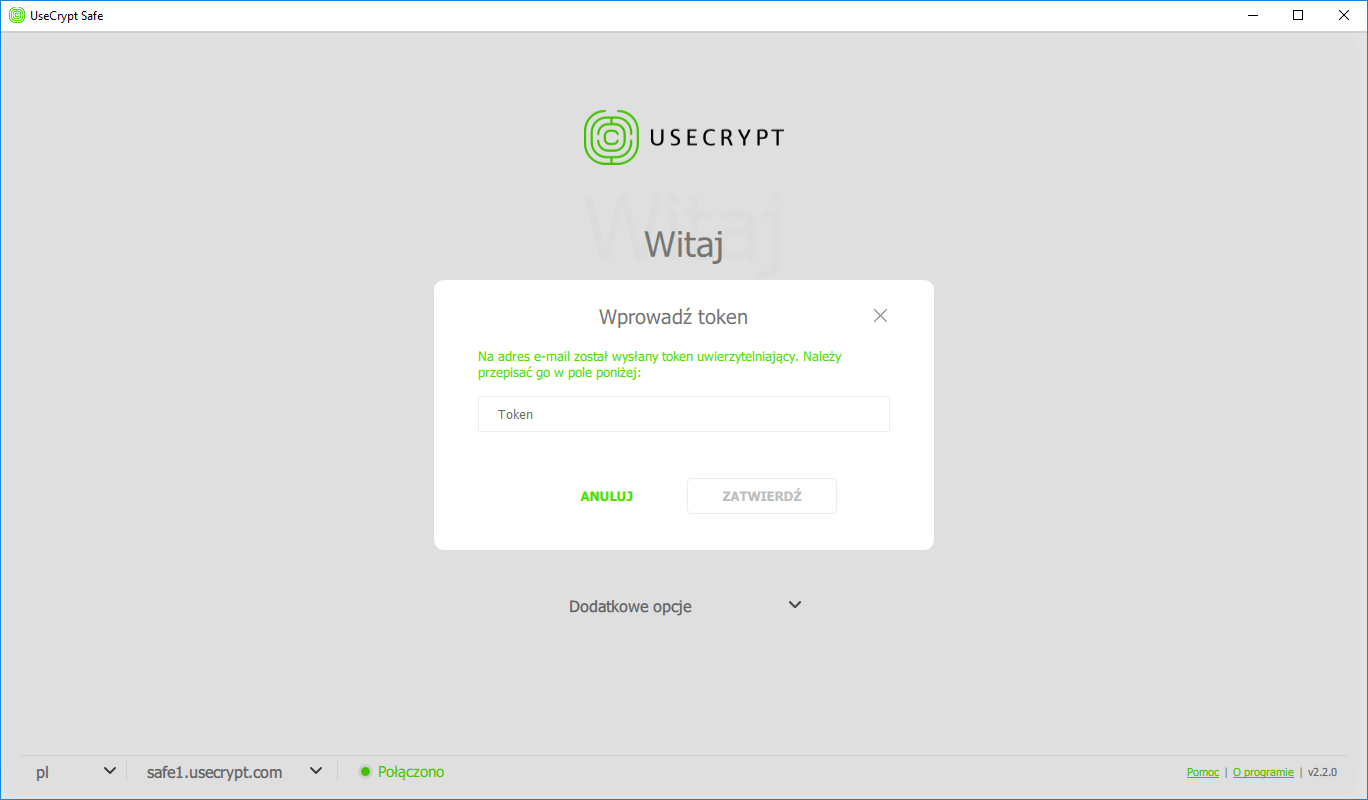
The UseCrypt Safe application is protected against dictionary attacks. This means that when a laptop computer is stolen, after 10 failed attempts to log in, the user account is blocked and must be reactivated with a token. The token, in turn, is sent by email:
The administrator of an organization that has a UseCrypt Safe on-premises server has an even greater level of control over security. A lost or stolen device can be deactivated in the administrator panel or from another device of the same user. This results in deactivation of only the selected device, with other devices of the same user remaining active.
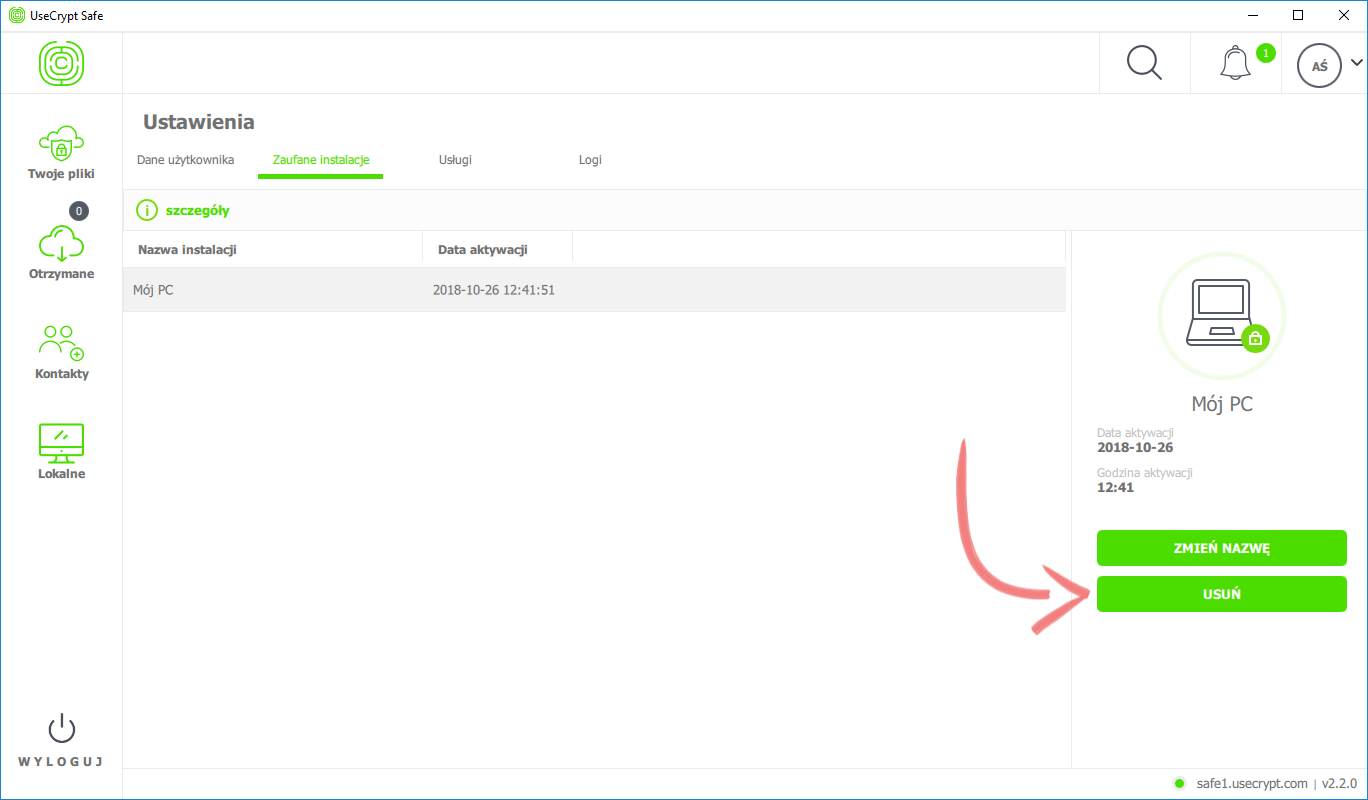
If the incident is reported in a timely manner, full control of access to files is guaranteed. The conditions of good protection of data include the aforementioned password but also many additional factors – only correct authorization of the user (password) on the machine (token) on which the user configuration is present (a half of the private key encrypted with a key that the server provides after correct authorization) makes it possible to log into the account. If those conditions are not met, access to applications and files is not possible.
It is the user who decides whether copies of files are to be kept on the computer’s drive or only in the cloud. In order to further improve the security, local files can be deleted and their encrypted versions can be stored in the cloud (or both in the cloud and locally). Files can be read only after the UseCrypt Safe application is installed.
Transfer of documents is very easy. One needs to select the file and the recipient from a list of contacts (other persons who have a UseCrypt Safe account). Only in this manner can one automatically send to another person the cryptographic key needed to decrypt a message.
The technology used in UseCrypt Safe has been implemented on Dell computers that have the application factory-installed. As a result, organizations are ready right away to fulfil one of the requirements related to safe data storage specified in the GDPR. Data in the cloud is saved in the UseCrypt infrastructure on servers of the IBM Bluemix class and, similar to the UseCrypt Messenger messaging application, the UseCrypt Safe application offers encryption both in the cloud and in the customer infrastructure.
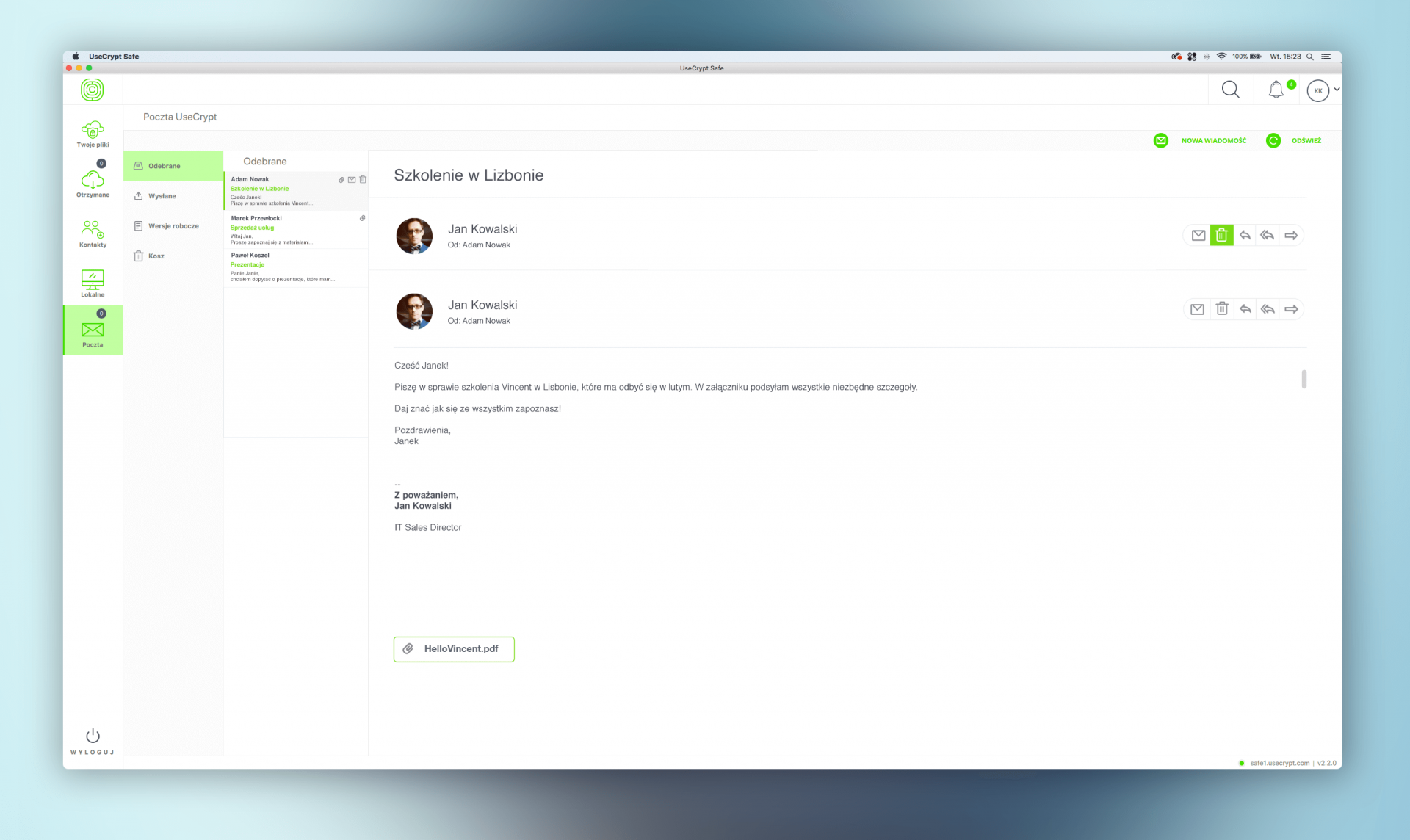
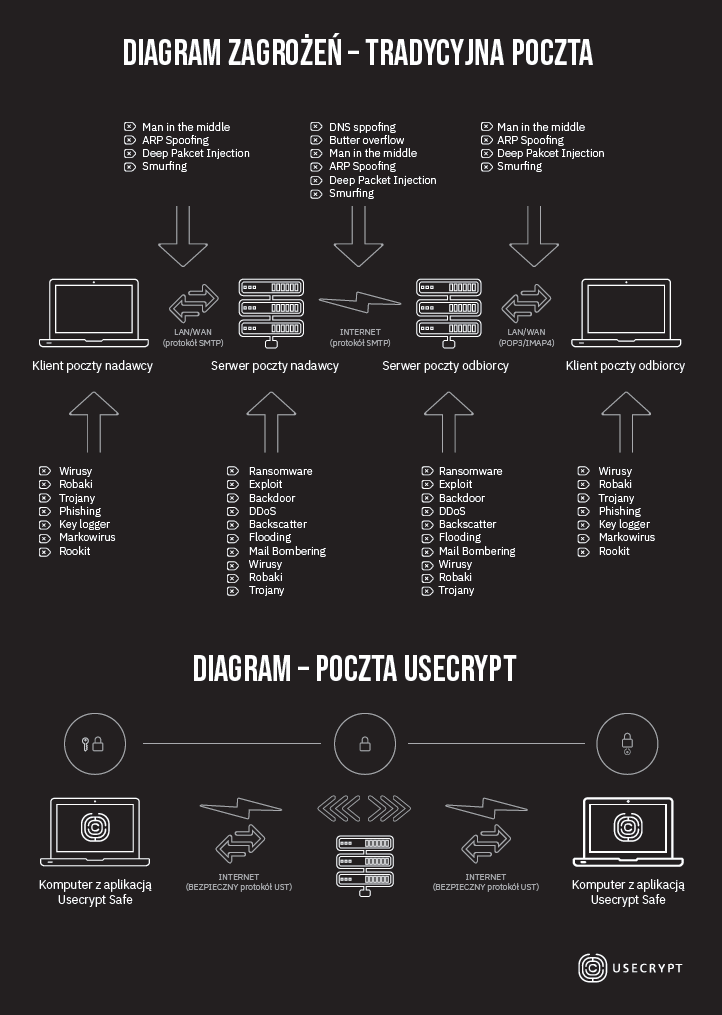
Emails are not sent by a separate mail client. It is UseCrypt Safe that is responsible for encryption and sending of text and attachments in safe channels. Sending emails using UseCrypt Safe is SAFER and EASIER than using traditional encryption with a PGP key because, technologically, the product of the Polish company not so much provides better protection using additional algorithms as the communication between the sender’s computer, the email server, and the recipient’s computer is safer than sending/receiving email through the SMTP/IMAP4 protocols.
In conclusion, in a traditional email message sending process, the sender’s computer is exposed to malware, MITM attacks, and ARP Spoofing. The sender’s computer, the email server, and the recipient’s computer can be attacked and disclose the content or the attachment of a message (the cache of email clients is not encrypted and enables easy readout of contents, even if PGP encryption is used). Moreover, the third-party supplier of the email service (e.g. Gmail), which is the email service administrator, has the technical ability to read emails if they are not encrypted. If emails are sent sing the UseCrypt Safe, the sender’s computer, the recipient’s computer, and the server of UseCrypt S.A., even if they are infected or attacked by a hacker, do not have all the cryptographic information to decrypt the email message content or attachments at the same time.
The email functionality was introduced into the software quite recently. During a visit at the software developer’s office, we were assured that adding the encrypted email sending function is consistent with the natural vision of development of the application, which is being implemented by engineers in cooperation with customers, and meets customers’ demand for such services.
Technical aspects of the UseCrypt Safe. Strengths and weaknesses
For the diagram below, a step-by-step description of file encryption, from the local computer, through the software developer’s server, to the recipient’s computer, was prepared.
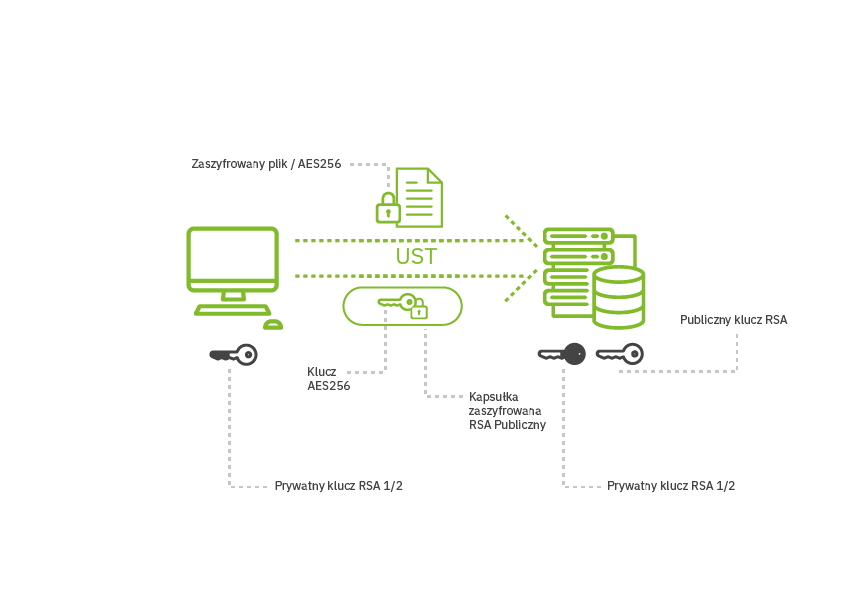
- A public key and a private RSA-2048 key are generated at the time of account registration. The private key is divided into two parts, in accordance with the HVKM rules. One part is saved locally in the user configuration and the other is sent to the server. From that point on, use of the private key always requires cooperation of both parties: encrypted information must first be decrypted by the server, then decrypted by the client, and then it becomes fully decrypted.
- Files on the user’s computer are encrypted using the AES-CBC-256 algorithm using the random key K, which is encrypted with the user’s public key using the KEM mechanism (the so-called capsule).
- The cryptogram of the file and the capsule with the key are sent to the server; the server does not have physical access to the encrypted data and, consequently, one can be sure about its security.
- Keys are sent between the server and the computer by the proprietary UST (UseCrypt Secure Tunnel) protocol which replaces the SSL/TSL protocols due to their numerous susceptibilities. Communication is encrypted using the AES and requires confirmation of the identity of the server based on a certificate issued by UseCrypt CA. On the other hand, key exchange is effected using the commonly recognized DH method (Diffie-Hallman is a combination of the names of cryptographers who developed this protocol). The UST has an advantage over, e.g. VPN tunnels, as it operates in the application layer and prevents eavesdropping or spoofing by other applications started on the user’s computer. Unlike the SSL/TLS, the session key (agreed in the authentication protocol) is generated not only on the client’s side but also on the server side; this provides an additional protection in situations where the randomizer on the customer’s side is of low quality (which may make it easier for the attacker to guess the password).
The strength of the RSA asymmetrical algorithm lies in the mathematical problem related to finding two divisors of a large prime number which, when multiplied, produce that very large prime number. Multiplication is a fast process for computers but division is not; therefore, in a natural computation process, it has not been possible to decrypt a key that is 2048 bits long (this length is most often used in ransomware). It is estimated that a 2048 bits long key will be attack-proof for 10 more years but it will be easy to replace it with a key of greater length, e.g. 2096 bits. Factorization computation is an excessive load even for contemporary quantum computers. This is actually good, because it must be computationally difficult to obtain a private key based on a public key. If a public key is provided, no one should be able to calculate our private key on its basis, because this would lead to disclosure of the unique part of the cryptosystem and a possibility to decrypt all files that have been accessed.
Because the weakest link of the RSA algorithm is the need to protect the private key, the software developer implemented additional protection layers. Most of all, a part of the private key that is sent to the server is divided by the unique HVKM (Hybrid Virtual Key Management) technology, registered in the European Union Intellectual Property Office and the International Office of the World Intellectual Property Organization in the USA. Thus, the company holds patents for the use of the HVKM technology in five member states of the EU and in the USA. The second part of the private key is on the user’s computer.
In the other direction, a file can be decrypted only when the computer and the server are connected online simultaneously, i.e. the data downloaded by the user is decrypted first by the server and then by the client. Consequently, no third party can by itself perform cryptographic operations without access to the second part of the key, even if the software developer’s servers are compromised or if the user’s computer is infected or attacked. Even if a hacker gets a hold of a part of the user’s key, he cannot decrypt the user’s data without cooperation of the server, which requires correct authorization. In the case of standard algorithms, e.g. the PGP, if the user’s key is stolen, encrypted data can be accessed. Consequently, when another person receives documents, he or she must download the UseCrypt Safe application in order to automatically receive a file with the public key that was used to encrypt files on the sender’s computer and is needed to decrypt files on the recipient’s computer.
Does this sound complicated? Perhaps it does: files were encrypted and placed in the UseCrypt cloud. Neither the software developer nor the administrator is technically able to access the data because they do not have the second unique part of the private key necessary to decrypt the files. Of course, they can attempt to perform factorization of the public key but so far only a 768-bit key has been broken. UseCrypt Safe uses a key that is 2048 bits long. Also, not only files but also file names and directories are encrypted on the server; consequently, no-one can even guess what the content of a document is. Files saved in the encrypted format (*.enc) are saved in a selected directory on a computer and/or in a cloud. The only thing that a third party can see is the size of the encrypted file.
In case of loss of access to a device, during registration the so-called rescue configuration is also created. This process is invisible for the user. The purpose of the rescue configuration is to provide the ability to recover access to an account if the configuration or the password is lost.
The procedure of recovery of access to an account using the rescue configuration involves setting a new password and cancelling the authorization of all previous Trusted Installations and the current pair of RSA keys. This means that if a user has several devices, he or she will not be able to log in on those devices until repeated authorization is performed. Such configuration file can be exported to a file but this is not recommended due to the possibility to lose it. It is best to use the integrated remote configuration transmission mechanism and to add a new device to the Trusted Installations.
Each time a user logs into the UseCrypt Safe, the computer must have access to the current User Configuration file. Consequently, it is not possible to log into the application using another device. A third party that learns a user’s password and email address (used as the user ID), cannot log into the application using another device. Another computer can be added by authorization with a token sent to an email address. In the case of corporate environments, it is recommended for the rescue configuration and its password should be secured by the IT department which has the competencies needed for their safe storage and use.
In conclusion, the technology and encryption used in the UseCrypt Safe provide:
- Safe transmission even when a device or a server is compromised (after a break-in);
- The sender’s private key required to decrypt his or her files is not stored on the server or the computer in its entirety. The disadvantage of this solution is the required Internet access when accessing files, if the files are not stored on a local hard drive.
- UseCrypt Safe can store files on the software developer’s server or on the company server.
- As a default, files are sent to the UseCrypt server on the 10352 port. In an on-premise installation, the port can be changed in any other port.
- One cannot log in on another computer without first authorizing the device. This is a very good method that protects accounts against access by unauthorized persons.
Conclusions and questions to the software developer
When analyzing the weaknesses and strengths of the UseCrypt Safe software, it is hard to find any of the former. Even though it is a pity that the software developer has not covered mobile application, it claims that this is due to the fact that such an advanced application would be hard to transfer to a mobile system. We find it hard to believe it, but it is hard to make any arguments against this statement without knowledge of the technical aspects of the application. Having finished our discussion of the weaknesses of the software (yes, it was short), we can describe its multiple strengths.
Let us start with security. Security of files and of the very communication between the client and the server has been thought-through and is properly ensured. The central point of encryption is responsibility of the RSA algorithm and the patented unique HVKM technology, which divides the private key into two parts. Without both parts of the key, neither cybercriminals nor the software developer can decrypt the files. The UseCrypt application enables the users to keep non-encrypted copies of files on a local hard drive; therefore, such files may be stolen in the event of a cyberattack. It is up to the user to decide whether he or she wants to keep local copies in an unencrypted form. Important data stored on a computer hard drive should be encrypted or stored only on a server in the cloud where data replication makes it possible to protect information against a failure of the server.
API. The software developer provides not only the application but also its technology. An API makes it possible to use file encryption and communication on any project. Such projects may involve services similar to file exchange or online accounting services that encrypt attachments (invoices and scanned documents). Members of management boards and staff working in remote locations can use the technology for safe circulation of documents. Employees of government administration bodies and politicians, on the other hand, can use the technology to send financial data. Government security agencies, the police, and the fire brigade can securely communicate using the UseCrypt Messenger messaging application and larger industrial companies can use this technology to safely send information between SCADA systems. Essentially, the technology used in UseCrypt can be used wherever there is a risk that communication or data is captured, e.g. in IoT devices, in production processes, in smart cities, or in car systems. The technology can prevent personal data leaks, which may result in sanctions pursuant to the General Data Protection Regulation (GDPR). A good application for the software is digitization (archiving) of documents and backup copies – non-encrypted backups contain complete knowledge about a company.
Thanks to the software developer’s invitation to visit its branch in Warsaw, we could learn a lot about UseCrypt Safe and ask additional questions:
1. Can you tell our readers about your plans related to future updates of UseCrypt Safe?
The modifications that we are currently working on or that we are planning for 2019 are:
- a plugin for Outlook, both in the Windows version and in the MacOS version;
- expansion of the functionality of UseCrypt Mail:
- withdrawal of emails;
- signatures (email footers);
- inbox catalogs;
- filters;
- formatting of text messages;
- pausing and resuming file transfer (this is particularly useful in the case of large files);
- a synchronized directory (SyncDir);
- transfer in the background;
- context menu;
- corporate functionalities for customers with more than 500 licenses.
2. For what practical tasks and most urgent tasks can/should small and large companies and government institutions use such a product as UseCrypt Safe?
The greatest strength of UseCrypt is the security it provides and the fact that only the data owner can access data his or her data. The digitization process that every company and state institution will sooner or later undergo is a big challenge to IT departments, as they need to identify ways to ensure security and the place where data will be stored, taking into account the situation in large corporations worldwide. The UseCrypt cloud ensures full protection of digitized data and full accountability of who has access to the data and when.
3. What do you provide access to, as a part of the API, to companies that would like to use your technology.
In the current version, the API is available to our selected customers as automation of certain processes. Our team of analysts helps our customers define the problem and take actions that will facilitate and speed up the performance of certain tasks. Thanks to the API and automation, we can eliminate various errors caused by employees and, consequently, perform some operations for example during the night when the „load” on the Internet connection is smaller.
The UseCrypt Safe application has won a COMPUTERWORLD award in the Best In Cloud category in 2018 for the best product and supplier of cloud solutions.
The UseCrypt Safe application has received a recommendation from the Military Technical Academy and the National Institute of Telecommunication. The software was checked by ethical hackers working for the consulting-auditing company Deloitte. They were supposed to hack a server and decrypt the stolen data. Of course, they were not able to access the data.
Additional information about UseCrypt Safe can be found in an interesting and comprehensible PDF leaflet prepared by the software developer and on the https://usecrypt.com website.
Czy ten artykuł był pomocny?
Oceniono: 0 razy





