We have recently published the list of recommended free antivirus suites. All recommended free antivirus suites are poorer versions of their commercial counterparts, with some exceptions. Of course they don’t provide as good protection as specialized solutions. In this summary, we have developed a list of recommended security suites which should be carefully considered by every Internet user. Developers of solutions from the following list of paid antivirus products for 2019 had to earn a good opinion and a graphical recommendation from AVLab. We recommend to every user solutions with at least a good rating. Differences between individual antivirus suites are sometimes very subtle, and occasionally so large that the choice can be very difficult. Notwithstanding a decision, in order to get to know all features of each application, you should at least try out 30-day trial version.
When selecting the best specialized protection solution for 2019, we recommend a cold calculation. If you have any question or doubts, we encourage you to take a substantive discussion in the comment section below.
Recommended paid antivirus suites of 2019 for micro-businesses and home users (SOHO)
Software had to meet at least one condition in order to be on the list:
- Providing a license for commercial use and/or the retail market.
- We haven’t taken into account commercial software with a temporary promotion for “0 PLN”.
- Providing at least good protection based on our tests and external tests.
The following mini-reviews, general recommendations, and final assessment have been developed not only on the basis of the results achieved in various test categories. The following descriptions are supported by experience in the sector which we specialize in. We ask for substantive criticism in the comment section, if we’ve made a mistake somewhere.
Here is the list of security suites recommended by AVLab:
- Arcabit Internet Security
- Avast Premier
- Avira Antivirus Pro
- Bitdefender Total Security
- Check Point ZoneAlarm Extreme Security
- Comodo Internet Security
- Emsisoft Anti-Malware Home
- Eset Internet Security
- F-Secure Total
- G Data Total Security
- Kaspersky Total Security
- mks_vir internet security
- Quick Heal Total Security
- SecureAPlus Premium
- Sophos HOME Premium
- SpyShelter Firewall
- Symantec Norton Security
- VoodooShield Pro
- Webroot SecureAnywhere Internet Security Plus
Here are the best and recommended by the AVLab editorial team paid antivirus suites for the year 2019 (in alphabetical order).
ARCABIT Internet Security
- Country of origin: Poland
- Technologies used: own and Bitdefender
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows and Android (Arcabit Home Security)
- Developer’s website: https://arcabit.pl
- More information about Arcabit: https://avlab.pl/producent/arcabit
Arcabit Home Security is the code name of the same suite as Arcabit Internet Security, available in a variant for 3 or 5 devices, additionally including protection for the Android system. Arcabit software was definitely a niche product back in 2013. Since then, the developer has done something unbelievable. He has completely rebuilt the application code achieving a much better performance. The know-how needed for effective protection against threats have begun to be provided by an experienced team who have managed to get out of the shadow with this security suite within a few years. A very good suite. We think that Arcabit currently plays a leading role in the theater of antivirus companies.
We appreciate Arcabit software for a flawless and 100% protection against malicious scripts. By default, the suite doesn’t allow dangerous commands to run in the Windows interpreters, that’s why it achieves maximum results in many of our test. We can say that modern techniques of infecting operating systems are ineffective against Arcabit products. Simply put – non-technical people are perfectly protected against malicious attachments, including macro viruses, as well as other malware samples. The developer has rightly left himself a certain margin of error in the event that files would have been encrypted (you can see how the SafeStorage module works in this video: https://www.youtube.com/watch?v=f0MD7CE13V8).
No doubt Arcabit strong point is a browser and email protection. The original mechanisms of the developer are supported by the Bitdefender engine and signatures that detect known malicious software. The greatest strength of Arcabit are algorithms that block macro viruses and JavaScript downloaders. Besides, the SafeStorage module allows a user to restore files after encryption (even in network resources). A secure browser for online banking is a module equipped with unique techniques against malware, and shouldn’t be ignored. All these advantages ensure that we value the Arcabit solution very highly.
Recommendations
The antivirus settings are appropriate. We have no objections to default recommendations. We recommend more technical user to enable an interactive mode in a firewall and network resources scanning for the SafeStorage module.
Rating
![]()
We recommend security suites from Arcabit to all users who want to support local developers and appreciate the high effectiveness of protection at a reasonable price.
AVAST Premier
- Country of origin: Czech Republic
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://avast.com
- More information about Avast: https://avlab.pl/producent/avast
It’s true that free Avast is the most often chosen protection for computers in Poland (often unwittingly). Paid applications of this company are a completely different league and taking into account their price, they aren’t so popular. The latest version adds support for hardware virtualization which is protection against malware getting out of a sandbox. It also has protection against ransomware, which applies for files located in preselected folders on a user account profile in Windows. We really like a test environment included which is available in the context menu. In a sandbox, we can right-click to run any software and check suspicious attachments or downloaded files without worrying about security. The second interesting feature is a firewall. Connections for applications have been graphically presented here. They are sorted by developer (for example, Microsoft, Google, Oracle). This interesting visualization of connections allows a user to adjust the levels of traffic in both directions using graphical sliders.
Recommendations
The default configuration of Avast Premier is good, but it isn’t the best. We recommend enabling “hardened mode”. Even the developer says that this is the option for inexperienced users, so why it has been disabled? The hardened mode launches unknown file in a virtual environment, analyzing suspicious changes. This mode is safe and proactive method of blocking new malicious software and 0-day threats that can deceive antivirus technologies. Additionally, an automatic repair for potentially unwanted programs should be activated in the protection settings.
Rating
![]()
We recommend Avast software with the “hardened mode” and protection against PUP enabled to users who expect antivirus to respond effectively to emerging threats. With the network of over 400 million devices, the developer can guarantee it. Like other providers in this region, Avast users are protected as a priority against threats emerging in Europe.
AVIRA Antivirus Pro
- Country of origin: Germany
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://avira.com
- More information about Avira: https://avlab.pl/producent/avira
The Avira software has always maintained a good level of protection. In our tests, it has dealt well with drive-by download attacks. This is one way to infect computers that’s invisible to a user. Without comprehensive protection, it isn’t possible to defend against such sophisticated attacks. The Avira software has again received the best result in another test examining areas of protection against ransomware, cryptocurrencies miners, and new threats related to the WSL feature in Windows 10. The Avira Antivirus Pro security suite has a significant advantage over its free version, very popular, and liked by Internet users. Paid software has a higher priority for access to the Avira Protection Cloud where suspicious samples uploaded from infected computer are analyzed. In recent months, threats classified as cryptojacking are particularly burdensome. It’s worth noting that the Avira Browser Safety extension not only protects against malicious IP addresses and domains that spread malware. The module can also detect and block tracking scripts, advertisements, and scripts mining cryptocurrency. In the case of blocking ads we are dealing with a list provided by AdGuard. The Avira Browser Safety for Chrome, Firefox, and Opera makes it considerably easier for non-technical users to interact with a computer. The developer reports that in the first three months of 2017, the Avira products detected 1,4 billion threats. And that’s paradoxically good news. In our tests regarding protection against malicious software, a browser-level protection module has stopped almost all threats. In turn, other technologies operating in real time protect against attacks. These are an anti-ransomware module, an email protection, a firewall, and an unknown threats scanning in the cloud. The developer has recently stepped into the market to secure Internet of Things devices and home appliances. Avira SafeThings router has been presented.
Recommendations
The developer has positively agreed to our recommendations and has activated by default protection against macro viruses and disk scanning in a network location. It’s also worth enhancing the heuristics by switching the AHeAD (Advanced Heuristic Analysis and Detection) technology setting to an aggressive level.
Rating
![]()
We recommend Avira software to users who appreciate the German sturdiness, a multimillion community, and a company with traditions and experience.
BITDEFENDER Total Security
- Country of origin: Romania
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://bitdefender.pl
- More information about Bitdefender: https://avlab.pl/producent/bitdefender
Bitdefender is one of the leaders in the security industry. This is the undeniable fact that has been confirmed by ranking, ratings, comments, tests, and popularity of the SDK. The software is difficult to judge purely from the perspective of the previous series. The corporations expansion into European markets was initiated 10 years ago. More or less from that time, Bitdefender antivirus began to systematically occupy high positions in security rankings. And to this day, engineers don’t slow down – they keep pace with the best, and sometimes set new trends. End users, who use products from this Romanian developer, shouldn’t have any reasons to complain.
Let’s put aside such banalities as “protection against ransomware”. The strength of this suite is based on over 500 million community, the largest of all developers in the world. The mean people describe such a large community as a botnet, but without anonymous data about threats from millions of computers, it would be impossible to protect users against 0-day threats in less than a few seconds. This means that if at the other end of the world Bitdefender detects a threat, all of its clients will be immediately protected against the attack.
Bitdefender is known for providing its technologies to other products. There’s a reason that it’s so valued all over the world. Non-technical users can install the application and forget that they have a very comprehensive suite. They will find, for example, a vulnerability scanner that automatically updates the operating system and software. Connection to a bank or PayPal account must be secured so the suite contains the Bitdefender Safepay browser which provides a real-time protection against scams, phishing, viruses, and malware, including viruses that intercept keyboard keys, and viruses that can take screenshots and upload them to a server of a criminal. The Wi-Fi Security Advisor is another addition included in the price – Bitdefender checks whether a wireless network that, for example, a laptop, smartphone, automatic vacuum cleaner, and IP camera is connected to, has been secured with strong cryptographic codes. Files encryption protects data from getting into wrong hands. Created container can be blocked at any time. Each time a computer starts up, a user will be asked to enter a password for the container (for security reasons). A strong password to a folder with files can be generated in the password manager and stored there safely.
Improvements in 2019 version in the field of network attack prevention and technology of filtering websites guarantee that it’s very difficult to find a malicious website. Additional security in the form of in-depth scanning of all traffic makes it difficult to circumvent the Bitdefender antivirus protection.
The Bitdefender Total Security is such an comprehensive suite that it’s hard to mention all its advantages in a short description. You can find the full review at this link.
Recommendations
Bitdefender Total Security is optimally configured. We don’t have any additional recommendations.
Rating
![]()
We recommend Bitdefender software to all users. The product can operate completely automatic without asking any questions. So it will work wherever a computer is used as a tool for work that shouldn’t interfere.
CHECK POINT ZoneAlarm Extreme Security
- Country of origin: Israel
- Technologies used: own and Kaspersky Lab
- License: for individual and commercial use
- Availability of basic languages: English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://zonealarm.com
- More information about Check Point: https://avlab.pl/producent/check-point
The ZoneAlarm Extreme antivirus software is the response from the Check Point company specializing in providing network security and protection of individual users and administrators who would like to protect their privacy and entrust a system security to the developer with many years of experience. Check Point is known for solutions which high quality is confirmed by constant presence in the Gartner square and very good results in the NSS Labs tests. Check Point solutions secure 100 thousand companies and 90 million users around the world.
ZoneAlarm Anti-Ransomware benefits from the experience of Check Point company. A Threat Emulation technology is available in this product. Check Point ZoneAlarm Extreme Security benefits from Check Point employees experience who provide services for large business. We have recently tested the Threat Emulation in the form of extension for browsers. Product from this company was the only one who has stopped all malicious software samples. The full set of the Treat Emulation technologies is available in advanced firewalls or as a SaaS service under the name Check Point Sandblast. ZoneAlarm Extreme Security is characterized by excellent protection against ransomware. Malware authors can create samples that can easily bypass security of traditional signature products. A threat detection based on virus definitions is an old technique for detecting known attacks. Currently, it serves better as support than being a protection core. In contrast, the threats emulation protects against new encryption malware. This is technology used by the Check Point ZoneAlarm Extreme Security.
The product is characterized by two more things. A unique firewall that protects, among others, against modifying HOSTS files. It protects against Internet attacks, and also allows a configuration of restrictions for access a network directions of application. Its effectiveness is confirmed by two tests carried out by AVLab where the commercial software of ZoneAlarm has received a recognition. The second unique thing is protection in a browser thanks to a threat database from the ThreatCloud system. It’s a huge organized network for fighting with a cybercrime which provides data about threats and attack trends based on a global network of threat sensors. The ThreatCloud database identifies every day millions of malicious software. It contains over 250 million addresses analyzed for bots detection, over 11 million malware signatures, and over 5,5 million infected websites.
Recommendations
In urban areas with a high density of wireless networks, we recommend to enable protection against poisoning ARP tables in the firewall module settings.
Rating
![]()
We recommend software to users who wants to have a high level of protection. ZoneAlarm Extreme Security gets the best results in the tests carried out by AVLab.
COMODO Internet Security
- Country of origin: USA
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, iOS, Android
- Developer’s website: https://www.comodo.com
- More information about Comodo: https://avlab.pl/producent/comodo
Comodo Internet Security is a powerful tool to protect the operating system against 0-day malware and hacker attacks. Comodo Internet Security as a full security suite often outperforms the effectiveness and functionality of commercial products from other companies. It’s important to emphasize (although it’s archival information) that a few years ago the CIA tested the majority of well-known antivirus applications, but only one of them particularly got under hackers skin who worked for the agency. The Comodo suite has gained a term of “hard to hack” antivirus.
Comodo Internet Security is also available in a paid version as Comodo Internet Security Pro and Comodo Internet Security Complete. In addition to an advanced antivirus engine with implementation of an automatic threats detection and a classification technology, we will find many more features here. The most significant are an automatic sandbox that runs suspicious files which the antivirus engine and cloud scanning haven’t been able to identify on time as trusted. The automatic sandbox protects against 0-day threats which the antivirus engine won’t be able to detect through signatures or scanning files in the cloud. As befits a top-shelf product, a website scanner is available here. The origin of files (Internet, external drives, network resources, etc.) is very important in protecting against unknown threats which are treated with an increased risk of potential infection. A cloud analysis (based on white and black lists) and the HIPS are supporting modules that monitors system and applications activity to ensure that potentially dangerous file performs certain actions that can be reserved for malicious software. On the other hand, the Viruscope, active by default, is a behavioral component for analyzing and monitoring processes for potential malicious modifications. The Viruscope is able to rollback malicious modifications of the system settings.
Comodo Internet Security has a secure shopping module. This functionality allows to enable a virtual environment for online transfers, unknown applications, or invoices. A user has at its disposal a fully-fledged system that works “next” to the Windows system and can without fear for the security, for example, run suspicious attachments and check their threat level. The Secure Shopping contains protection against keyloggers, trojans, worms, screenloggers, and also isolates processes preventing a malicious code injection into a browser in the virtual environment, and also checks the validity and expiration date of the SSL certificate. According to the AVLab editorial team, one of the most undervalued modules is a firewall. In this respect, Comodo has a lot to offer. It contains the specialized firewall for scanning Internet traffic which protects against ARP spoofing attacks. Technical users will appreciate the creation of very detailed rules for packet filtering. A graphical representation of processes that refer to Internet resources is an additional value.
Few people know that the Comodo Internet Security antivirus can be managed from a console in the cloud in the Comodo ONE Home Edition solution. The protected systems include Windows, Android, and iOS. The additional advantage of Comodo ONE Home Edition is the remote removal of installed applications and monitoring of devices status, including utilization of RAM and disk space in real time. In case of theft, it’s possible to remotely locate a stolen device, send an sound alarm command, block a device, or erase data.
Recommendations
The developer has prepared three sets of preconfigured settings: Internet Security, Proactive Security, and Firewall Security. Internet Security is the default mode, but the most secure is Proactive Security because it contains, among others, the HIPS module enabled, and has the least “open gates” for malicious software.
Rating
![]()
We recommend Bitdefender software to individual users as well as micro entrepreneurs who receive and very good protection for workstations for free. The commercial version of Comodo Internet Security Pro includes free technical support and a $ 500 refund in the event of infection. On the other hand, the Comodo Internet Security Complete version includes an additional 50 GB of storage in the Comodo cloud and 10 GB of monthly transfer for TrustConnect Wifi Security (Comodo VPN).
EMSISOFT Anti-Malware Home
- Country of origin: New Zealand (previously Austria)
- Technologies used: own and Bitdefender
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, Android
- Developer’s website: https://emsisoft.com
- More information about Emsisoft: https://avlab.pl/producent/emsisoft
In the tests of security products for small and medium-sized enterprises and individual users, Emsisoft software has been repeatedly awarded for excellent behavioral protection in real time and impeccable performance of the products.
Through the WannaCry ransomware, threats of this type have been placed on the list of security teams. It turned out that the entire IT world isn’t prepared for massive attacks that use vulnerabilities in software and file sharing protocols, and clearly ignores good security practices. The reasons for this lack of professionalism can be found in the shortage of competent professionals or inadequate knowledge about attack vectors. Emsisoft was one of the first developers who has been behaviorally blocking WannaCry, without having signatures developed. The company takes responsibility for security and claims that still remains a technological leader in the fight against malicious software which encrypts files. It’s hard to deny the developer’s enthusiasm and willingness, because there’s plenty of truth in it. For 16th year in a row Emsisoft confirms that only the best can stay on the market, adjusting to rapidly changing trends. The Emsisoft software has recently received the Emsisoft Browser Security extension for browsers that puts privacy first. Instead of uploading full URL address of each website to the cloud for verification, it calculates a hash of the website, and then it compares patterns with threats matching the calculated hash function. This means that Emsisoft doesn’t log any details about browsing activity and oversteps when it comes to privacy.
In the application we can find a log for reading all events and activities related to the operating system, installed applications, but also malicious software. This functionality has been added for both individual users and the Emsisoft Enterprise Console. Centralized management allows administrators to easily read logs from workstations and find the core of the problem in the case of hard to predict system failures caused by a user, malicious software or an operating system. The log allows to observe all warnings about suspicious websites and applications, as well as how they are handled by both a user and a operating system. It’s possible to check when exactly the malware analysis is started and when it’s completed, together with all consequences. Emsisoft Anti-Malware Home doesn’t have a firewall. It’s replaced by a behavioral monitor that warns a user with a message when an unknown application attempts to access the network. The technology has been developed since the oldest version of the software, and allows to block attempts to manipulate Windows firewall rules.
Recommendations
We don’t have any additional comments regarding the recommended settings.
Rating
![]()
We recommend flawless and easy to use Emsisoft software to all who want to use the install-and-forget type of suite, and targeted to respect for privacy.
ESET Internet Security
- Country of origin: Slovakia
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://eset.com
- More information about Eset: https://avlab.pl/producent/eset
In general, Eset has been maintaining a high level of protection for many years through the Live Grid cloud and a very good detection of potentially unwanted programs. ESET products have a feature which blocks threats that try to activate and attack a user right after turning on a computer before booting the operating system – this is so-called UEFI scanner. Original mechanisms have been receiving very good ratings for many years, confirming the effectiveness of their security. A well-configured firewall module makes the biggest impression already in the default mode which detects malicious communication used by botnet networks. Not without significance it blocks “ARP spoofing” attacks that allow hacker to capture data sent within a local area network, as well as “DNS cache poisoning” network attacks in which an attacker sends false information to a DNS server that associates a domain name with an IP. The two-way firewall containing Intrusive Detection System guards data and detects attacks poisoning ARP tables and modifying DNS entries, fake PING queries, attacks that exploit SMB, RPC, RDP protocols and scan ports. It’s obvious that the developer mentions such safeguards in its advertising material, but the most important thing for end users is that everything just works.
Another useful feature is “ESET Banking & Payment Protection” that secures WinAPI of the operating system against key interception, so a user is protected against manipulation of data entry at the browser level when typing bank account numbers or logging into online bank account.
Less technical users should use “Connected Home Monitor”. In public places, it checks if an access password to a router is strong enough, identifies devices connected to a router, and provides an insight into unknown devices nearby. Then it’s worth to watch out and disconnect with such network or connect to the Internet using the VPN tunnel. Moreover, “Connected Home Monitor” indicates a gateway address, i.e. the IP address of an access point through which devices communicate with the Internet in a local network. Less technical users to which this module is addressed will gain insight into devices located near an access point. The ESET security suite is very extensive software. You can find the full review in a separate article at: https://avlab.pl/nowy-eset-internet-security-na-rok-2018-pod-lupa-avlab-z-konkursem-dla-czytelnikow
Recommendations
All recommendations are provided in detail at the link to the review above. So we enable the detection of potentially unwanted and dangerous applications in advanced scanner settings. We enable the detection of viruses written in high-level languages (mainly scripting) and zipped programs in real-time protection settings. We also enable document protection which is very important, but it’s disable by default. Encryption viruses are often smuggled this way.
Rating
![]()
Is ESET a good choice? It’s solid, good, but there are areas which require a little more work. Perhaps it’s better because the developer won’t rest on his laurels until he reaches perfection. Fighting cybercrime is essentially a continuous improving getting to know an enemy.
F-SECURE Total
- Country of origin: Finland
- Technologies used: own and Avira
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://f-secure.com
- More information about F-Secure: https://avlab.pl/producent/f-secure
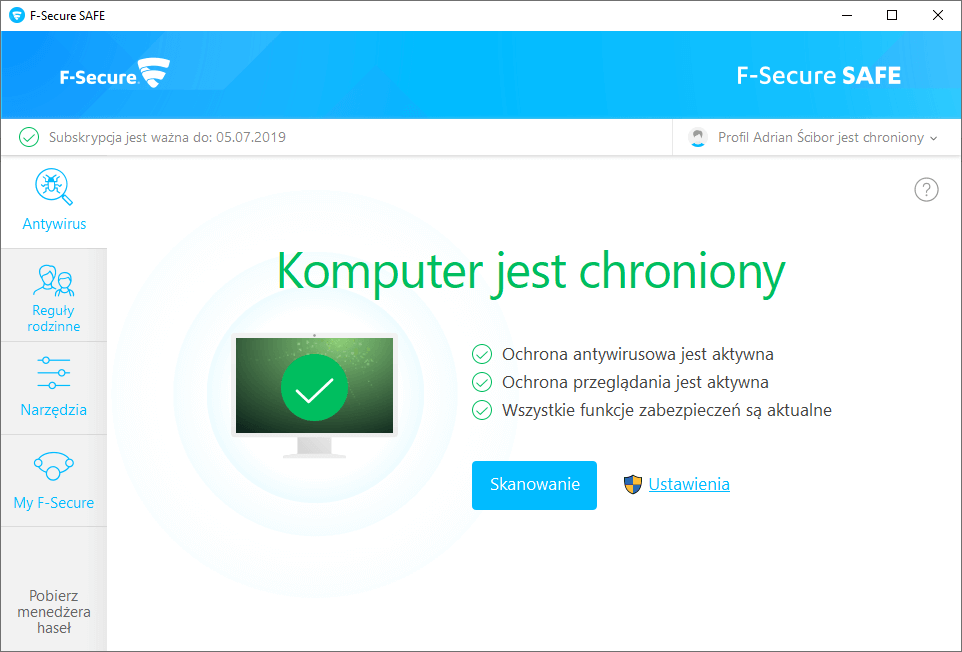
F-Secure TOTAL, or rather F-Secure SAFE + F-Secure Freedome (VPN) from this whole list is characterized by extraordinary concern for privacy. In the suite, besides an advanced antivirus, we receive annual access to an unlimited transfer to network encryption through one of dozens of available VPN servers. F-Secure TOTAL includes:
- F-Secure SAFE antivirus. This solutions provide protection against malware that secures online banking sessions, and enables parental control which sets up rules for time spent on the Internet by children.
- F-Secure Freedome VPN. It’s software that encrypts network traffic, providing anonymous and safe use of the Internet on devices with the Windows, Android, and iOS systems.
- F-Secure KEY password manager which protects passwords and PIN codes.
The strength of the TOTAL suite is the DeepGuard technology embedded in the antivirus engine. It’s a kind of behavioral-based security that monitors selected folders for suspicious behavior. In the case of risk detection, a dangerous process is automatically blocked and a user receives a warning about a potential threat. The DeepGuard verifies application security based on information from a trusted external service. When the application security can’t be verified, the DeepGuard begins to monitor the functioning of the process. The DeepGuard is able to detect new trojans, worms, software vulnerabilities, and other malicious applications that try to make changes to the computer, and also prevents the suspicious applications access to the Internet. This is original technology from the F-Secure developer. Potential harmful changes in an opearting system that are detected by DeepGuard technology include: changes in the system settings (Windows system registry), attempts to disable important system applications – for example security software, and attempts to edit important system files. The technology not only protects against ransomware, but also blocks applications that could replace, rename, or delete important files.
F-Secure offers a whole range of products. When it comes to software solutions, we have at our disposal the Quad9 service, i.e. DNS servers with IP address of 9.9.9.9. The Quad9 works as a protection filter and completes a “black list” of malicious websites identified by F-Secure and other partners providing information about threats. When a device or application tries to connect to a domain which is blacklisted, Quad9 blocks translation of domain name into IP address, and informs a user that a website has been identified as malicious. The Quad9 services supports the DNSSEC protocol to protect users from attacks using so-called DNS poisoning (sending fake information associating a name with an address to DNS servers) – this attack can be described, for example, as a replacement of the bank website by hackers.
When it comes to hardware solutions, there is F-Secure Sense, a router for home and commercial use. F-Secure SENSE is much more than a traditional router, because it’s distinguished by its luxurious design, but also on the technological side, it doesn’t look like the cheapest models from electronics stores. The SENSE devices, just like a real hardware for threat management, is equipped with several unique modules whose aim is to protect against malicious software of home network and all other devices with built-in network card connected to the router.
F-Secure is one of the leaders with regard to the privacy of users. Łukasz Tasiemski, leader of the F-Secure research center located in Poznań, asked directly whether he would agree with the sentence […]:
“F-Secure doesn’t share any data enabling identification of a user who uses the F-Secure software”
[…] he has no doubts, giving as an example a real incident which Polish law enforcement authority was dealing with – the police contacted the headquarters in Helsinki, requesting information about a particular F-Secure Freedome user, because it was noted that a crime was committed from a server located in Warsaw belonging to the VPN of the F-Secure Freedome software. F-Secure headquarters have refused to cooperate with the police representatives, arguing that first of all, F-Secure sends to the developer servers fully anonymous information that don’t allow users to be identified. Secondly, even if it was possible, F-Secure wouldn’t share any client data. Finland is a country with many facets, and one of them is the liberal superior law that holds the welfare of the individual above the community.
Recommendations
We don’t have any additional recommendations regarding the configuration of settings which don’t allow much anyway. The only thing missing is the more aggressive settings of the DeepGuard module, and lack of an interactive firewall. Unfortunately, the Deep Guard can’t work in the prompting mode when applications establish network connections (the technology works automatically).
Rating
![]()
We recommend F-Secure software to all users who value their privacy in the Internet, and want to use the install-and-forget type of suite, and don’t want to give up the trouble-free security suite.
G DATA Total Security
- Country of origin: Germany
- Technologies used: own and Bitdefender
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://gdatasoftware.com
- More information about G Data: https://avlab.pl/producent/g-data
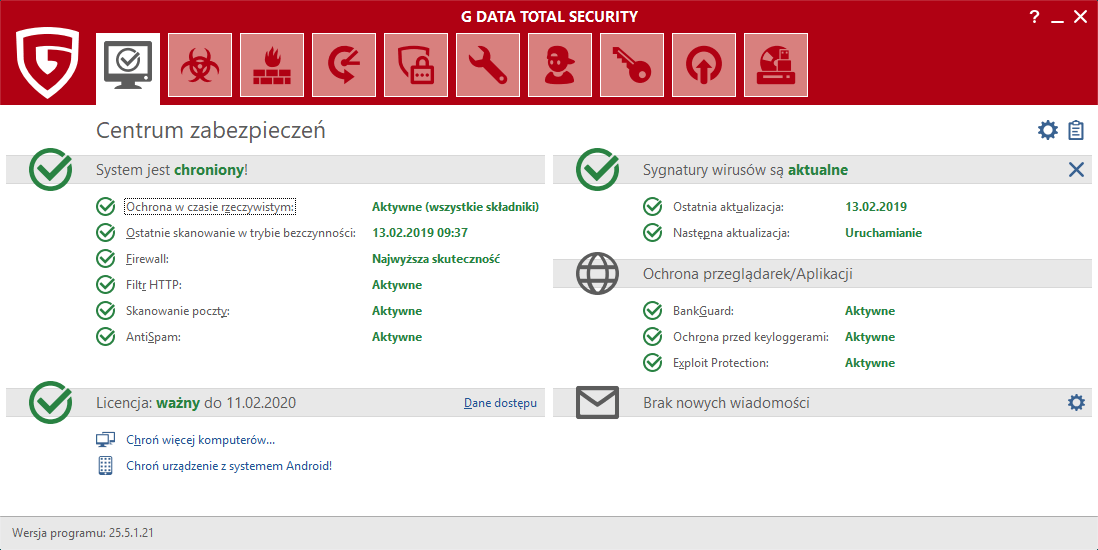
G Data Total Protection is a very well developed security suite that protects against online attacks and threats. At the security center, a user will find information summarizing data from other modules. For security purposes the most important components are a firewall and antivirus protection, covering most protocols, including the new DeepRay technology. Based on many years of experience , experts have developed new methods of detecting malicious code. They can determine which of a combination of factors are potentially harmful, for example, presence of jump instructions in PE headers, the ratio between executed code and file size, specific file compression methods, or even number of imported system functions. In this aspect, the complexity of protection consists in covering all protocols through which user communicated with the Internet. DeepRay uses machine learning to detect malicious code, regardless of the manual analyses carried out by specialists in the field. Experts have developed a self-learning system based on machine learning that detects well-disguised malicious software. So DeepRay “was taught” to analyze malicious code and calculate risk taking into account over 100 factors. On safety features, G Data provides high-quality software that will satisfy even computer geeks.
Suitability of additional modules actually depends on how a computer is used. An office worker will be satisfied with a well-developed anti-spam filters integrated with Thunderbird and Outlook email clients. Computer gamers will appreciate the full automation of the suite which doesn’t ask questions, and allows for the so-called hardening of system settings using a graphical wizard (a system and applications will be set to the highest security, privacy, and SSD performance). On the question of data security, an encryption module is available which meets requirements the RODO directive in terms of safekeeping data by micro entrepreneurs. Any files or data can be stored in such encrypted container. They will be safe and available only after entering a password.
For the youngest Internet users, the developer has prepared a parental control which includes blocking websites with violence, eroticism, drugs, and other categories. It’s possible to define time spent using a browser, or generally a computer. Software on default settings is addressed to the majority of Internet users, so the lack of technical knowledge doesn’t pose any problem.
An interesting fact is that in 2010 G DATA signed the “No backdoor” under the ”IT Security made in Germany” voluntary action of the TeleTrust association. The company has voluntarily undertaken not to leave any vulnerabilities available to exploit by special forces, and not send or forward any data. The G DATA company clearly declares that it rejects all proposals of “cooperation” with special forces.
Recommendations
We recommend switching the firewall to the highest efficacy mode, leaving the autopilot settings.
Rating
![]()
G DATA Total Security is very reliable software, especially on custom settings. We recommend to advanced users, and those less technical.
KASPERSKY Total Security
- Country of origin: Russia
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://kaspersky.com
- More information about Kaspersky Lab: https://avlab.pl/producent/kaspersky
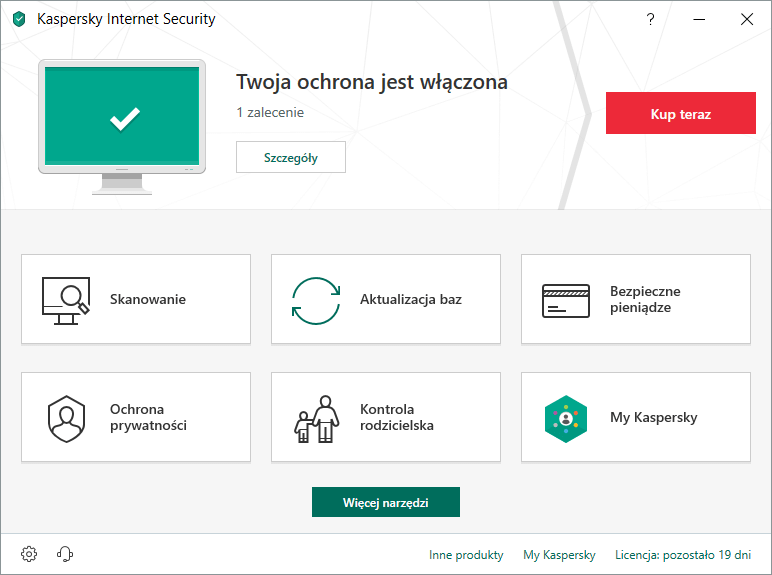
Kaspersky is based on advanced technologies which continually achieve the best result in independent tests (and according to the AVLab tests provide very good protection). Kaspersky uses the Kaspersky Security Network to obtain information about reputation of files and applications. Through processing information about threats in the cloud (with all devices secured by Kaspersky Lab products), it’s possible to react more quickly to new threats and reduce false alarms.
In terms of the demand for system resources, Kaspersky is performing very well. A few years ago, many users were complaining that Kaspersky Lab’s products consume RAM and CPU. Since at least three versions, Kaspersky Lab have done something that other developers could follow. Performance test carried out by AV-Comparatives confirm that the software which heavily burdens the operating system, in three years have been equipped with one of the better the resources management system.
Kaspersky is extremely robust software. Not only, it doesn’t cause problems with computers, but it protects devices at the highest level. It has a firewall that filters network activity, a webcam protection that prevents tracking, and network attacks blocking module. It has malware monitoring, for example, ransomware through the “System control” module. The “System control” collects data about application activity on a computer, and share those data with other modules in order to provide better protection. In Kaspersky Lab’s commercial software, a rollback can be initiated by file protection or scanning. In this product it’s possible to rollback malicious modification, for example, after a ransomware attack. Protection of opened and modified files, communications protection that scans messages for malicious links, and email protection are distinguishing features of this product. Website scanning for phishing and malicious resources, including dangerous scripts is another value that draw our attention. The Safe Money is a very important module. It suggests opening a secure browser resistant to injecting malicious DDLs, or even reading confidential information from RAM inserted into a browser. An attacker or malicious software can’t obtain a login and a password or replace the content (amount, bank account, etc.) of banking transactions by displaying on a user’s screen fake windows imitating a real website. He is also unable to take screenshots, register keystrokes, and mouse clicks. Any attempts to take screenshots are also blocked, including screenshots of the entire desktop using API functions such as GDI, DirectX, or OpenGL.
Besides the advanced antivirus, Kaspersky Secure Network VPN is installed during installation process which allows encryption of network traffic, not exceeding 300 MB of daily transfer.
Recommendations
Kaspersky is optimally configured. We don’t have any comments regarding the default settings. A user can experiment with a more aggressive configuration of heuristic analysis.
Rating
![]()
We recommend the software to individual users. Kaspersky Lab have been providing the highest quality protection technologies for over 20 years. The company specializes in detecting ATP attacks by security critical infrastructure of banks, industry, public institutions, and consumers around the world.
MKS_VIR internet security
- Country of origin: Poland
- Technologies used: own and Bitdefender
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows and Android
- Developer’s website: https://mks-vir.pl
- More information about mks_vir: https://avlab.pl/producent/arcabit
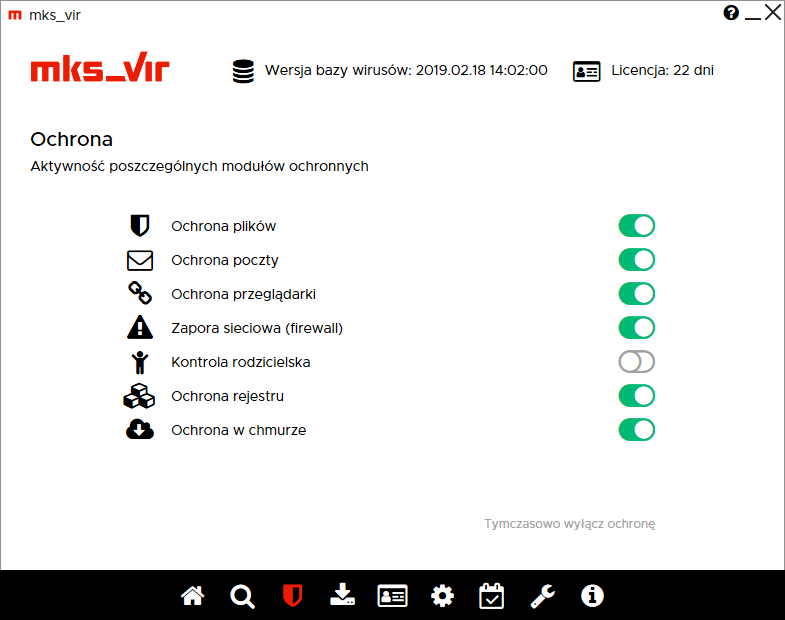
Protection in the mks_vir internet security suite is implemented by original technologies developed by Arcabit (mks_vir antivirus brand belongs to the same Warsaw company). It contains an heuristic antivirus engine, firewall with interactive mode, and also great mechanism which blocks macro viruses and fileless malware. A very important preventive component is the SafeStorage technology: if a virus managed to encrypt a user’s data, the mechanism would be able to recover data automatically. In practice, the SafeStorage is an encrypted storage on a computer disk where a backup is created when files are modified, written, or deleted (accidentally or intentionally). The idea behind the creation of the SafeStorage is to protect important data – various types of documents, graphic files, databases, sheets. It can recover modified files, encrypted by ransomware, or deleted by malware in a short time. The SafeStorage and the module available in the suite allowing for creation of encrypted disks take on particular importance in the context of the EU regulation, i.e. personal data protection legislation.
The full review of mks_vir is available on the website: https://avlab.pl/antywirus-mksvir-wystarczy-ci-na-kolejne-500-lat
Recommendations
The antivirus settings are appropriate. We have no objections to the default recommendations. For more technical users, we recommend enabling interactive mode in the firewall and network resources scanning for the SafeStorage module.
Rating
![]()
We recommend mks_vir security suites to all users who want to support local developers and appreciate the high effectiveness of protection at a reasonable price.
QUICK HEAL Total Security
- Country of origin: India
- Technologies used: own and Bitdefender
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, macOS, Android, iOS
- Developer’s website: https://quickheal.com
- More information about Quick Heal: https://avlab.pl/producent/quick-heal-seqrite

Quick Heal antivirus software actively monitors downloaded files and components that could become a potential attack. It analyzes in a real time file behavior in the operating system through the DNAScan technology. It creates data backup that can be restored to the state before encryption in the event of protection failure. This copy is encrypted with an internal algorithm developed by Quick Heal, so that data are protected from an unauthorized access by the third party. The Quick Heal solution is a multi-layered security suite. As befits uncompromising protection, Quick Heal deals very well with spyware, adware, keyloggers, trojans, and other malware.
If we must mention a protection component which is often overlooked and underestimated, but has an important function in the protection, it’s a firewall with built-in protection against intruders (IDS/IPS means Intrusive Detection System / Intrusive Protection System). The Quick Heal includes has a similar IPS/IDS system for protection against intruders as the Quick Heal Seqrite UTM Terminator hardware product which is designed for medium and large enterprises. The feature of blocking unauthorized attacks is enable by default.
Why is a firewall with built-in IPS/IDS module so important? In advanced attacks where more sophisticated methods than social engineering are used (these are mainly attacks on unprotected and outdated protocols, for example, SMB), a firewall with IPS/IDS modules plays a very important role in security. A two-way firewall containing an intruder detection system can detect poisoning ARP tables attacks, fake PING queries, attacks that modify DNS entries, attacks on vulnerabilities of SMB, RPC, RDP protocols, and port scan attacks. It protects a home network against malicious software and stops malware before it installs on the operating system. It protects against downloading a dangerous file via CMD.exe or PowerShell.exe (these are system processes very often used in the malware code).
In the “Safe Banking” module, we really like a protection against replacing DNS addresses. There have been many cases when a router with poor security has been “hacked” by malware which were logging on using the administrator credentials. Replaced DNS addresses on a router caused the Internet traffic from devices in a local network to go through the attacker’s server. An unauthorized person could decrypt SSL communication and read logins and passwords, and replace bank websites or social networks. Data collected in this way could be used to attack friends of a hacked person. Using the Safe Banking module from Quick Heal prevents such attacks.
In the Quick Heal software, we can find one more feature enhancing protection. It’s “a browser” that runs in a sandbox. A default browser that user uses, is launched in a virtual environment inside an operating system. Right after a malicious website is opened, a virus is limited to virtual space and it’s not able to affect the functionality of the operating system (ignoring the scenario of escaping malicious code from a sandbox as a result of security vulnerability). After closing an application, all changes made in this environment will be removed, and won’t affect the functionality of an operating system.
Apart from that, we appreciate the software for protection against SPAM messages that works with installed email clients. It detects viruses and malicious hyperlinks in incoming and outgoing messages, and senders impersonating reliable entities. In addition, we have a scanner that detects outdated software which can be used to bypass safeguards. The mechanism can detect irregularities in the operating system settings. On competition of the work, it displays detailed information about CVE vulnerabilities identifiers which should be appreciated by users particularly interested in security.
Recommendations
The Quick Heal Total Security solution is optimally configured (besides anti-keylogger feature which should be enabled).
Rating
![]()
Quick Heal Total Security is easy to use and lightweight for the operating system. It contains a very useful IPS and IDS modules which distinguish it from competition. The software has a Polish language and is available for purchase in the official Polish distribution.
SECUREAPLUS Premium
- Country of origin: Singapore
- Technologies used: own, ClamAV (Cisco), and a dozen other antivirus engines in the cloud included in the UniversalAV technology
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows, Android
- Developer’s website: https://secureaplus.com
- More information about SecureAPlus: https://avlab.pl/producent/secureage-technology
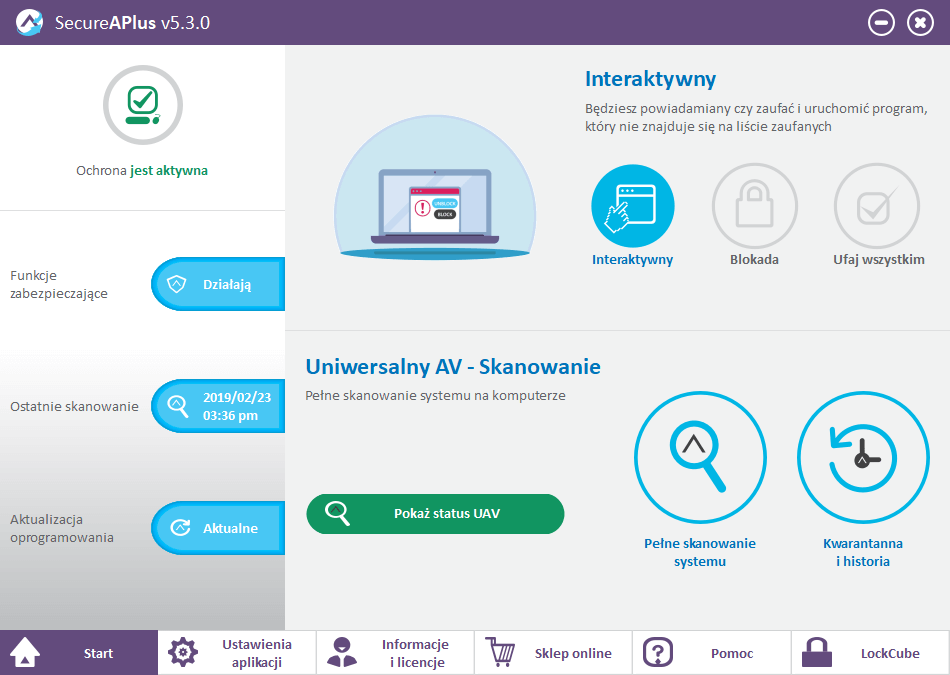
The protection model of the SecureAPlus application against malicious software doesn’t differ much from traditional antivirus. The developer still uses his own technologies, but also third-party engines in the cloud, to analyze files: AhnLab, AVG, Avira, ClamWin, Emsisoft, Eset, McAfee, Microsoft Security Essentials, QuickHeal, Sophos, and TotalDefense (the list may be changed). Detection and evaluation of files on the basis of additional scanning engines plays a secondary role and in fact, it fits into the whole protection as a “suggestion” for a user. This is very convincing suggestion that better defines security of applications than traditional “single-engine” antivirus. The Universal technology (12 engines in the cloud) is the amazing mechanism for effective detection of various type of threats.
The real advantage of SecureAPlus over traditional antivirus applications lies in a slightly different approach to protection – using trusted files lists and certificates providers. Data security is interactively verified by a user based on information about a checksum, digital signature of a file, as well as certificate providers collected by the developer.
SecureAPlus is available in Polish language, so using the tool is much easier. Secondly, SecureAPlus automatically scans all system files located on a hard disk right after installation, creating a secure database of files which have a digital signature of verified providers. If a user download a new file or tries to open an email attachment, SecureAPlus will display a notification depending on the situation. SecureAPlus is the powerful tool in the fight against malware in the hands of an experienced user. The software works very well, and doesn’t cause a performance problems. This is one of those applications that surprise very positively with the effectiveness of protection. The advantages of this product include numerous messages while installing legitimate programs. SecureAPlus analyses the behavior of running scripts, including CMD and PowerShell – the command line is also used by malware and installers of legitimate applications, so SecureAPlus can display prompts during these activities.
From November 2018, SecureAPlus has a new APEX engine that uses machine learning to detect malware which is no recognized by additional scanning engines in the framework of the UniversalAV. This is some kind of additional option of offline and online protection that will ensure the security if other third-party engines don’t detect a threat. The APEX is available in all SecureAPlus versions, including the Freemium version. The engine works both in the cloud and locally when user isn’t connected to the network. Additionally, the developer claims that the engine can work in conjunction with other antivirus engines. The APEX also participates in on-demand scanning.
SecureAPlus is available in the Freemium and Premium versions. The first one is free for 12 months. The Premium version additionally provides a technical support, and above all a higher priority when the UniversalAV scans unknown files (in the case of busy server, paid licenses have the higher priority).
Recommendations
The application is optimally configured and works in interactive mode, prompting a user in uncertain situations. For additional protection in the browser, we recommend installing uBlock Origin or NoCoin extension. The first one protects not only against scripts which use CPU cycles, but also blocks ads and malicious hosts forming part of domains involved in displaying malicious ads. The second only blocks scripts that mine cryptocurrencies.
Rating
![]()
We recommend the SecureAPlus application to users who expect security software to combine traditional technologies of scanning in the cloud with modern technologies of white lists and trusted certificate providers. SecureAPlus is a hammer for hackers and malware.
SOPHOS Home Premium
- Country of origin: United Kingdom
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: English
- Supported operating systems: Windows, Linux, macOS, iOS, Android
- Developer’s website: https://sophos.com
- More information about Sophos: https://avlab.pl/producent/sophos
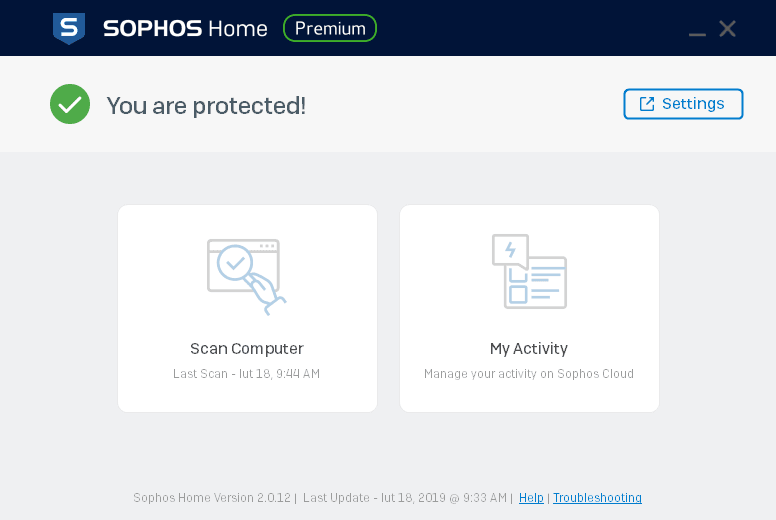
Sophos Home Premium uses a machine learning in the Deep Learning technology for detecting threats, so the same solutions used by the largest global companies protecting their interest through Sophos solutions. The software uses an artificial intelligence that can detect and block both known and new malicious software. Sophos Home Premium offers a real-time protection – preventing cybercriminals from exploiting vulnerabilities in trusted applications and operating systems or security credentials theft.
Through advanced anti-ransomware functions and other security features used in business-class solutions, Sophos Home Premium protects against constantly evolving cyber threats. The solution meets the requirements set by banks, governments, and companies around the world. Of course, the home version is a bit simplified, but nonetheless, Sophos Home protects against trojans, worms, bots, potentially unwanted applications (PUA), and the latest threats.
Sophos Home is equipped with a world-class embedded tool for removing malicious software and spyware cookies from an operating system. This is possible through integration of the HitmanPro technology – the legendary scanner which was bought a few years ago by Sophos company, and is constantly being developed as an integral part of the Sophos software.
Concerning online banking protection, the solution of the British company protects bank details and credit cards against interception by third parties. Sophos Home encrypts keystrokes in order to provide an additional layer of security. Nowadays, the vast majority of banking transactions take place on the Internet. Sophos additionally secures a browser. Besides a keystroke encryption, we’ve got constantly active protection against exploits, a detection of applications that access external hosts, and warnings against unauthorized code infection to a browser. All of these technologies work automatically and are enabled by default.
The solution can be configured only via a web panel. It’s not required to log into it every time, because the application has a unique link to the web console. This is an additional advantage, because Sophos Home Premium allows a user to easily manage the security of many computer from any place in the world. The console doesn’t restrict the antivirus configuration in any way. An amateur administrator can change settings or add exceptions to all modules included in Sophos Home.
Recommendations
All modules are enabled by default, therefore we don’t have any additional recommendations.
Rating
![]()
Sophos Home Premium is a very lightweight software, and in addition, it effectively warns against running unknown files that may cause problems with security. We recommend the solution to all users.
SPYSHELTER Firewall
- Country of origin: Poland
- Technologies used: own + additional scanning at Jotti.org + possibility of configuring any online scanner (e.g. VirusTotal)
- License: for individual and commercial use
- Availability of basic languages: Polish and English
- Supported operating systems: Windows
- Developer’s website: https://spyshelter.com
- More information about SpyShelter: https://avlab.pl/producent/spyshelter
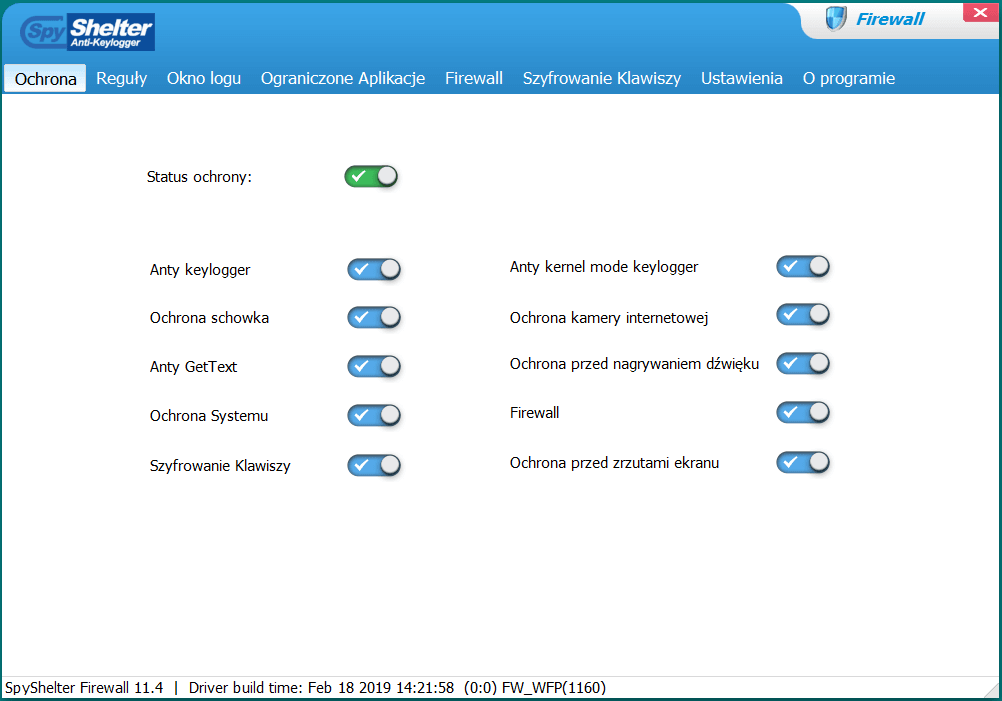
The SpyShelter software cannot be considered in the context of traditional antivirus protection. This isn’t application for blocking malware using developed vaccines or heuristic methods, and certainly not an application for blocking malicious content on websites. The power of SpyShelter Firewall lies in “observing” all processes and system services which through the synergistic effect create a secured workspace within the operating system.
If you intends to try the SpyShelter Firewall, ask yourself the most important question. Can we consider the application in the context of an antivirus protection? Will it properly protect against viruses? And if so, is it able to completely substitute antivirus software? Through the numerous features, the SpyShelter Firewall can completely substitute traditional antivirus software that protects computers in real time. Without a doubt, SpyShelter will work very well as the system guard, offering:
- system and files protection against modification, rootkits installation, code injection,
- system protection against keyloggers working at the kernel level,
- protection against capturing an image from webcam and sound from built-in speaker of the laptop,
- protection against screenshots,
- an advanced two-way firewall,
- increased resistance of selected applications to manipulation of exploits by limiting their access to files and registry, capturing keystrokes, and elevation of privileges.
The SpyShelter Firewall guarantees an operating system and data protection against the entire spectrum of malware (worms, spyware, keyloggers, ransomware), but it doesn’t perform these task in the same way as traditional security solutions that detect anomalies on the basis of behavioral heuristics. The fundamental and most important difference between the SpyShelter Firewall and “ordinary” antivirus is the method of detecting those anomalies – deviations from functioning of processes, operating system, and installed third-party applications.
The software provides a preventive approach to the security and uses advanced techniques to detect and block data breach attempts. Defensive actions may include alerting a user with messages and the cloud scanner. For the SpyShelter Firewall, threats such as keyloggers, spyware, or ransomware, aren’t viruses in the traditional sense of the word, but a sequence of inseparable events (actions) which notifies a user about. The SpyShelter Firewall doesn’t automatically remove malicious software, it can recognize files using the integrated antivirus scanner in the Jotti cloud (or other – it has the ability to configure an external file scanner). HIPS is just one defense layer that is part of the SpyShelter Firewall solution.
Recommendations
The default settings are optimal for most users. The software allows user to experiment freely. A sample configuration can be found on the website: https://www.safegroup.pl/thread-11669.html
Rating
![]()
The SpyShelter Firewall is a Polish solution that significantly deviates from known antivirus applications. If a user doesn’t want to use traditional antivirus, SpyShelter is the right software.
SYMANTEC Norton Security
- Country of origin: USA
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: English and Polish
- Supported operating systems: Windows, macOS, iOS, Android
- Developer’s website: https://symantec.com
- More information about Symantec: https://avlab.pl/producent/symantec
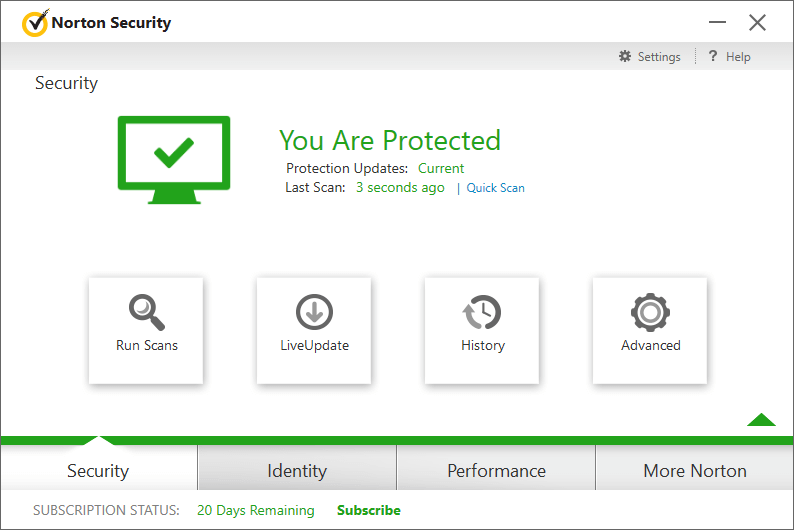
Norton Security is a very complex suite that uses a heuristic and proactive detection, providing an effective protection by detecting a suspicious application activity and also when downloading unknown files. It guarantees security at the higher level by detecting a destructive code and protection against unknown threats for which no signatures have been released. The SONAR protection helps to remove traces of malware attack, and restores damaged system files to their original state.
A firewall with the IPS/IDS technologies is a very useful module. It blocks hacker attacks and unauthorized traffic by monitoring communications between computer and other computers in the network. It informs about incoming connections from other devices as well as outgoing connections made by applications located in an operating system. An additional advantage is the fact that it closes inactive ports, protecting against scanning them. The firewall scans a network traffic both incoming and outgoing, and compares transmitted information with the signatures database of the attacks. These signatures contain information allowing to detect an attack that exploits software or operating system vulnerabilities. When such data are detected by the module, the connection with a host is interrupted and a received packet is rejected.
The solution works well with a protection against unknown threats which is based on the files reputation. There is also protection for email protocols. The module contains antivirus protection, preventing viruses from moving into computer via email.
Recommendations
Norton Security is optimally configured.
Rating
![]()
The Symantec solution is fully automatic, and at the same time very functional, and has a specialized firewall with IPS/IDS module. We recommend it to every user.
VOODOOSHIELD Pro
- Country of origin: USA
- Technologies used: own, Cuckoo Sandbox in the cloud, a dozen antivirus engines in the cloud
- License: for individual and commercial use
- Availability of basic languages: English
- Supported operating systems: Windows
- Developer’s website: https://voodooshield.com
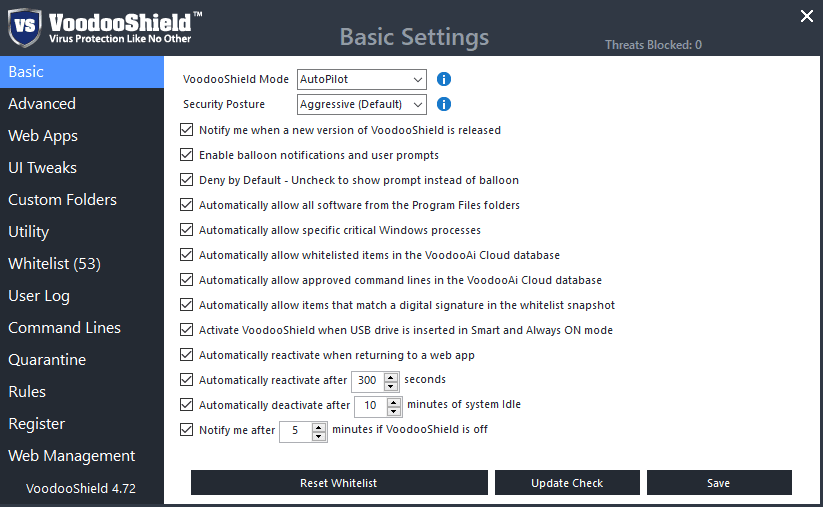
While traditional antivirus software can’t keep up with all vector and attack techniques, VoodooShield has no problem with that. It’s extremely effective against exploits. Through limiting the launch of new processes initiated, for example, by a browser, it doesn’t allow to execute a binary charge to exploit vulnerability. Although VoodooShield uses a list of safe files, unlike software based only on white lists, it creates a much more effective and robust blockade, offering several levels of protection. In the free solution right after installation, VoodooShield creates a small static list of running processes. In the paid version, a mechanism of creating a white list is additionally extended to the registry, folders, and software in use.
VoodooShield isn’t a traditional antivirus software. It also isn’t a traditional protection solution which uses white lists of files and applications. VoodooShield can’t even remove viruses from already infected operating systems (although the developer claims that this functionality may appear in the next versions). The true potential of VoodooShield lies in white lists of files, rules written by the developer and a user, as well as snapshots of the most important areas of the operating system. Through combination of several independent technologies, VoodooShield tightly seals the entire operating system against hackers and malicious software, with the help of patented technology.
VoodooShield uses its original, proactive approach to protection. It has a patented mechanism of automatic switching into a state of increased protection. By default, it operates in a “SMART” mode. The intelligent mode switches the protection to “ON” or “OFF” depending on whether a user uses Internet applications. In the mode of enabled protection (“ON”) VoodooShield is based on the developed rules: it allows critical system processes and applications from the „%program files%” folder to run automatically, practically reducing the number of prompts to zero. As befits modern software, VoodooShield uses the cloud in which it stores a white list of allowed applications what’s interesting – safe commands on the command line. Malicious software that attempts to, for example, download an additional resource from the network or extract virus modules using CMD or PowerShell, will trigger a warning message. If a user launches an executable file, he will receive information from automatic scanner which is equipped with dozens of antivirus engines. Then in the same dialog box, he can decide whether to block the file, leave it alone, move it to quarantine, or run it in the Cuckoo Sandbox – a website (malwr.com) similar to Virus Total and created by security enthusiast. The Cuckoo Sandbox is an open-source project. VirusTotal uses its heavily-modified version to analyze security of files and URL addresses.
If VoodooShield switches to the “OFF” mode, it won’t protect a computer in the traditional sense. This mode is automatically selected when we are installing applications which we don’t want to add to the white list. Additionally, it’s not required to run a file in this mode in order to check if it’s dangerous. VoodooShield has an on-demand scanning feature. In response, a user receives information about a status of infection based on instant analysis from dozens of antivirus engines in the cloud (it works really fast). The same applies to running scripts or suspicious commands in the command line – VoodooShield will display a warning with information about a digital signature of a file that has launched a command in the interpreter. Unfortunately, VoodooShield doesn’t display detailed information about names of the system commands, programs, files, or parameters of these commands, entered in the command line. This kind of information would be helpful and interesting from a technical point of view for advanced users.
The “AUTOPILOT” is the last mode recommended for gamers and users who don’t want to be bombarded with messages, but still expect the maximum protection. In this mode, VoodooShield automatically adds files to the white list that through the cloud scan have been verified as safe. If a file which is being verified isn’t on the developer’s white list and has been detected as a virus at least one time, VoodooShield will display a warning that will allow to decide what to do with this file: move to quarantine, run in the sandbox for analysis, or add to the white list.
Does VoodooShield need a lot of computer resources in order to work? Absolutely not. VoodooShield is extremely lightweight. It doesn’t scan anything in the background – on-demand scanning and running executable files are performed in the cloud. In turn, other potentially malicious actions, such as executing scripts or applications are based on white lists and rules created by the developer and a user.
Recommendations
Although VoodooShield provides extremely high level of security (not only against drive-by download attacks or locally launching suspicious executable files or attachments), however it doesn’t protect against JavaScript code running in a browser and mining cryptocurrency. It also doesn’t protect against phishing or malicious content on websites. For this reason, we recommend adding the uBlock Origin or NoCoin extension to a browser, but also the Bitdefender Trafficlight website scanner for uncompromising protection. Scanning technologies in a browser along with VoodooShield will be probably an unbreakable barrier.
Rating
![]()
We recommend the VoodooShield software literally to all users who have any technical knowledge and aren’t afraid to experiment. VoodooShield isn’t based on signatures. It doesn’t use behavioral analysis, so it can be installed next to another antivirus. But he doesn’t have to and actually shouldn’t be. VoodooShield can completely replace traditional antivirus software, significantly outweighing the effectiveness of the solutions available in this ranking.
WEBROOT SecureAnywhere Internet Security Plus
- Country of origin: USA
- Technologies used: own
- License: for individual and commercial use
- Availability of basic languages: English
- Supported operating systems: Windows, macOS, iOS, Android
- Developer’s website: https://webroot.com
- More information about Webroot: https://avlab.pl/producent/webroot
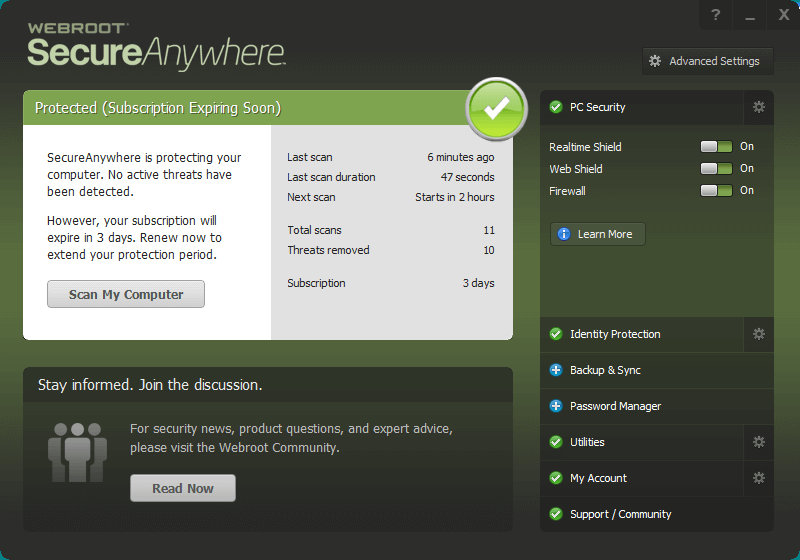
Webroot is one the leader in the American SME sector providing solutions for protection of workstations below 1000 licenses. The Webroot company based in the United States was founded in 1997 by two former employees of the NSA. Employees of this company specialize in providing innovative solutions in the field of protection of terminal equipment for millions of users from all over the world. Webroot has over 14 000 partners around the world. It protects over 300 000 companies across the globe (also in Poland), has hired over 600 employees, and it’s installed on millions of computers.
Webroot products make the most of the potential of the cloud computing. The antivirus agent doesn’t download signatures to a local disk (its size after installation is about 4MB), and file scanning is performed on the developer servers to achieve a better performance. On the other hand, OFFLINE protection uses well-known proactive techniques that don’t require an access to information about threats in the Webroot Intelligence Network to fight malicious software and suspicious software.
Let’s assume that a computer can’t access the Internet because of a network failure. How does Webroot secure user’s local files and protect a system against infection? When real-time protection in the online mode is active, all files on a disk are marked by Webroot as safe, malicious, or unknown. Dangerous files will, of course, trigger an antivirus alert and will be removed, while unknown files will be observed by Webroot on the basis of the DWELL TIME parameter. All actions performed by unknown files, i.e. creation / files modification / registry keys will be monitored by Webroot, and saved in the local event log of the antivirus applications. If the behavioral algorithm responsible for a behavior of files / applications in a system considers that an application performs suspicious activity and its behavior patterns match potentially dangerous software, Webroot will block such file / process, and on the basis of saved events in the local log rollback all malicious modifications made to a system using the Rollback module.
The difference between offline and online protection is diametric. When Webroot doesn’t have an access to the Webroot Intelligence Network in which information about threats is collected, it will have to deal with them differently. All new files located on the disk (and weren’t checked by Webroot earlier) will be treated as potentially dangerous, unknown. Even trusted installers or portable applications will be monitored and launched in a secure sandbox environment. Thanks to this solutions, the developer has proactively approached the issue of offline protection, and hence to situations where a typical “antivirus in the cloud” can’t refer to servers with information about threats.
Besides, Webroot is one of the lightweight antivirus applications in the world.
Rating
![]()
We particularly recommend it for computers that require high performance and good protection through modern technologies.
General recommendations from AVLab
The list of recommended security suites for 2019 from the AVLab editorial team probably contains all popular (and most of all) reputable solutions to secure the Windows systems. Some of them provide very tight protection by focusing on new scanning techniques, while others combine tradition with modernity.
We can confidently recommend solutions that have received at least good rating (4 stars) with the AVLab logo and the “Recommended” certificate. However, provided a user follow up on the recommendations.
All applications in the following ranking receive the recommendation from AVLab (alphabetical order):
- Arcabit Internet Security
- Avast Premier
- Avira Antivirus Pro
- Bitdefender Total Security
- Check Point ZoneAlarm Extreme Security
- Comodo Internet Security
- Emsisoft Anti-Malware Home
- Eset Internet Security
- F-Secure Total
- G Data Total Security
- Kaspersky Total Security
- mks_vir internet security
- Quick Heal Total Security
- SecureAPlus Premium
- Sophos HOME Premium
- SpyShelter Firewall
- Symantec Norton Security
- VoodooShield Pro
- Webroot SecureAnywhere Internet Security Plus
In addition, regardless of the solution chosen, we recommend to:
- Perform full scan of all disks immediately after installation. Owing to this, security state of a computer will be verified at the very beginning and an antivirus itself will work more efficiently.
- Install the uBlock Origin extension in a browser which blocks ads or JavaScript code that uses processor cycles to mine cryptocurrency.
- Install the NoCoin tool that is intended specially for protection against cryptojacking threats.
- If a product doesn’t have a firewall, it’s worth using, for example, the GlassWire firewall.
- It’s worth using VPN tunnels. A good VPN should always be active when performing payment operations on the Internet.
- Install additional protection in a browser. We particularly recommend the Avira Browser Safety and Bitdefender Trafficlight solutions which don’t cause problem in the form of false alarms. They don’t slow down websites. They guarantee very high effectiveness against malicious content, domains initiating drive-by download attacks, and cryptocurrency miners (even on seemingly “secure” websites marked with a green padlock)
You don’t want to pay for security suite? Do you need a free solution?
Check out our guide on free antivirus applications for 2019. It’s important to know that most of the free solutions described in this test aren’t nearly as effective as paid products (for example, VoodooShield Free and VoodooShield Pro differ diametrically), because paid solutions have the whole spectrum of additional functionalities. There are some exceptions to this rule – Comodo Internet Security and SecureAPlus. However, if the financial argument isn’t the primary criterion for the choice of protection, then the recommended security suites should be searched on the list in this article.
Additional information about guides and tests
If you have any questions, suggestions, or simply want to ask about security preferences – feel free to leave a comment.
We suggest all readers of this ranking that they shouldn’t only be guided by the rating. In order to make the final choice, we recommend that you read tests of other independent organizations which use various methods and techniques to test antivirus software. Furthermore, decision depends on personal preferences, availability of necessary functions, effectiveness, impact on system performance, interface design, price, ease of use, compatibility, language, technical support, and other factors.
Free solutions don’t meet your security expectations? We recommend you to read detailed reviews of other products: https://avlab.pl/polecamy, and also:
Guides:
- How to secure the entire home network by changing DNS addresses to those recommended by AVLab? (Guide 1, Guide 2)
- How safely log into websites? (Guide 1)
- How to protect your privacy on the web? (Guide 1)
- How to better secure Windows? (Guide 1)
And tests:
- Test of web browser extensions for protection against malicious software (Read more)
- The best antivirus software in 2019 based on three security tests (Read more)
- Test of software for online backing protection (Read more)
Czy ten artykuł był pomocny?
Oceniono: 0 razy





