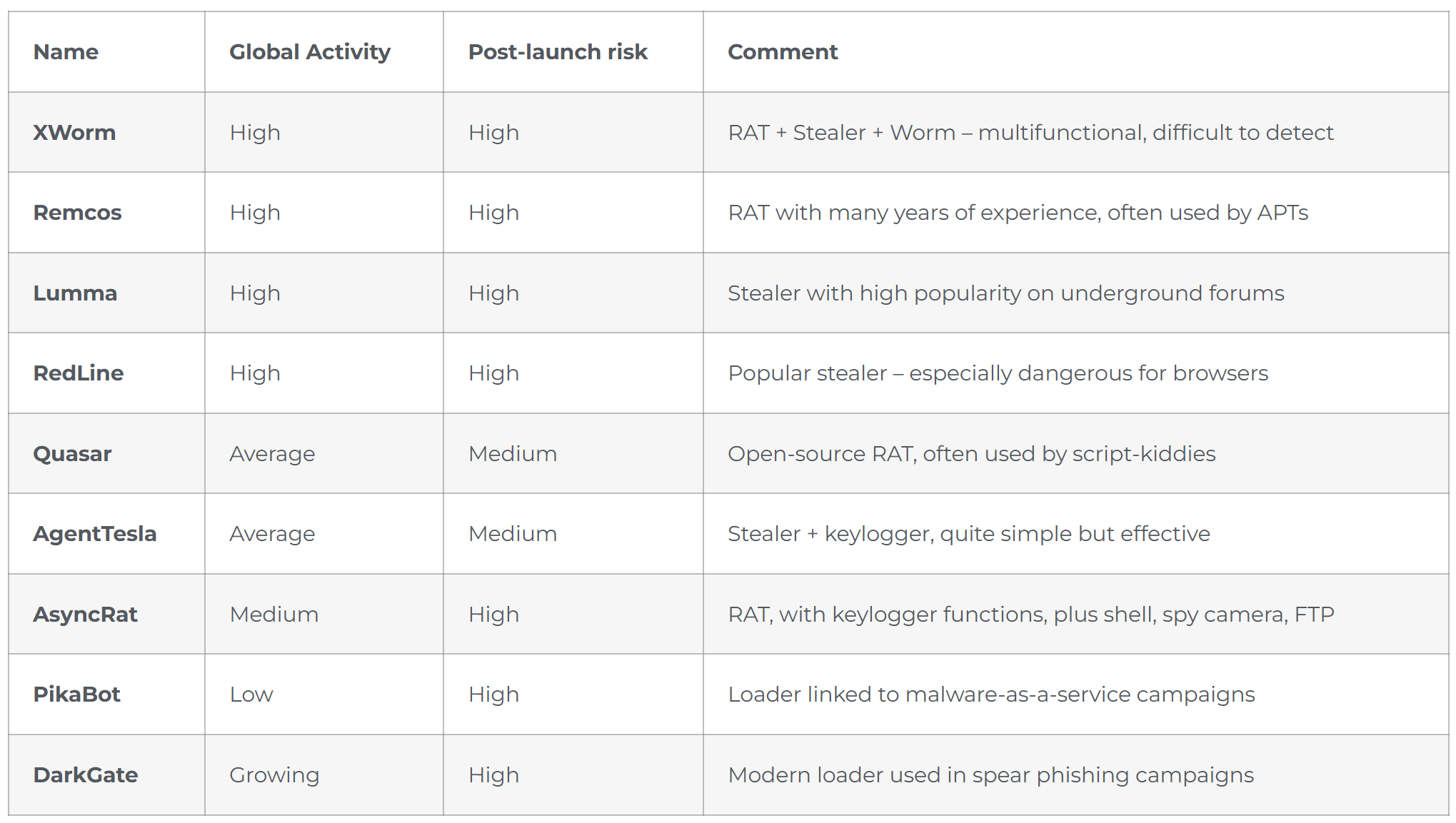
We publish the results from the second series of the long-term Advanced In-The-Wild Malware Test, designed to identify the best security solutions for protecting Windows systems at the end of the year. Throughout March, we tested 17 solutions to detect and neutralize real-world threats. The test included 607 unique virus samples found on the Internet, very fresh, 63 of which were hosted with encrypted HTTPS. Among the most interesting we can include:
Threat categories in this test by number of unique occurrences:
- Backdoor C&C (+200) – a general family of backdoors
- Keylogger (3)
- Credentials Stealer (37 samples)
- Tools used for hacking: kali_linux_tools for windows (4)
- Ransomware (16 samples)
- Trojan downloader (13)
- Banking Trojans (6)
- Remote Access Trojan (13)
Produced based on identified threats by two engines mks_vir and Kaspersky OpenTip.
In Advanced In-The-Wild Malware Test, we automate the activities users perform during their daily work with email programs, web browsers and instant messaging. At the same time, we realistically deliver URLs, recreate clicking on links, downloading and running files, and installing software to all Windows machines with security programs installed. Technical details are available in the survey methodology, and if you want to know more, just ask in the comments.
Our tests comply with the guidelines of the Anti-Malware Testing Standards Organization. Details about the test are available at this website as well as in our methodology.
What solutions did we test in March 2025?
What settings do we use?
Although we avoid using potentially unwanted samples (PUPs and PUAs) in the test, it is always a good idea to activate such a protection feature, and we do that too.
We always configure the protection solution to have a dedicated extension for the Firefox browser (if available). In addition, we set the entire software to automatically block, remove and fix incidents that occur.
Based on a series of tests already carried out, our opinion is that the predefined settings are good, but not always the best. Therefore, for full transparency, we list the ones we have implemented for better protection or if required by the manufacturer.
Enterprise solutions:
- Emsisoft Enterprise Security 2025 – default settings + automatic PUP repair + EDR + Rollback + browser protection.
- mks_vir Endpoint Security – extended http/https scan enabled
- ThreatDown Endpoint Protection – default settings + EDR + browser protection
- Xcitium ZeroThreat Advanced – predefined policy “Windows – Secure Profile v.8.1” + HIPS default action on “Block requests” + EDR enabled
Home and small business solutions:
- Avast Free Antivirus – default settings + automatic PUP repair + in-browser protection.
- Bitdefender Total Security – default settings + in-browser protection
- Comodo Internet Security 2025 – browser protection + block automatically for sandbox (block)
- F-Secure Total – default settings + in-browser protection
- K7 Total Security – default settings + browser protection
- Malwarebytes Premium – default settings + browser protection
- McAFee Total Protection – default settings + browser protection
- Microsoft Defender – default settings (does not integrate with Firefox)
- Norton Antivirus Plus – default settings + in-browser protection
- Panda Dome Advanced – default settings + browser protection
- Quick Heal Total Security – default settings + browser protection
- Webroot Antivirus – default settings + in-browser protection
- ZoneAlarm Extreme Security – default settings + browser protection + Anti-Keylogger enabled
Comments on the results
Advanced In-The-Wild Malware Test
- Average prevention level before triggering (PRE-LAUNCH): 57% .
- Average level of protection after the threat is launched (POST-LAUNCH): 42%
- Average response time to threats used in the test: 32 seconds
- Fastest overall average response time by a single vendor: 105 seconds (Emsisoft)
We evaluate the tested security solutions based on as many as 3 parameters:
- PRE_EXECUTION: is the malware file effectively detected and blocked at an early stage? This could be blocking a website or a file while saving, while trying to access the file.
- POST_EXECUTION: has the malware been downloaded to the system, run and blocked at the advanced analysis stage? This stage reflects the most dangerous situation and shows the real effectiveness of the protection software with the 0-day threat already active on the system.
- REMEDIATION TIME: has the threat or part of it been successfully eliminated? This parameter is related to the previous points and determines how long the malware stayed on the system until the security incident was detected and remediated.
Cybercriminals often use legitimate Windows components, so-called “Living off the Land Binaries” (LOLBins) to hide malicious activity. Based on the collected logs, we recorded the following number of instances of malware using legitimate processes:
- rundll32.exe – 3138
- certutil.exe – 2031
- schtasks.exe – 1999
- consent.exe – 1000
- tor.exe – 585
- powershell.exe – 288
The test showed that most of the analyzed solutions effectively block malware, with differences in response time and level of pre-launch prevention. Of particular note is the use of legitimate system tools (LOLBins) by cybercriminals to launch attacks, highlighting the need for advanced threat detection mechanisms.
About the Advanced In-The-Wild Malware Test
The test is conducted six times a year. It concerns testing security solutions for their effectiveness in blocking malware on Windows 11.
Tested solutions are evaluated based on three parameters: PRE_EXECUTION (early detection and blocking), POST_EXECUTION (advanced analysis and blocking after launch), and REMEDIATION TIME (threat elimination time). All of these stages are designed to indicate the product’s strengths in detecting and neutralizing malware. In addition, telemetry data is collected from the test to show the threat landscape and the techniques most commonly used by cybercriminals.
About AVLab Cybersecurity Foundation
AVLab Cybersecurity Foundation is a renowned organization affiliated with AMTSO and the Microsoft Virus Initiative that focuses on improving digital security through rigorous testing and analysis of security solutions. Known for their comprehensive methodologies, AVLab experts evaluate the effectiveness of various security products in real-world scenarios. By continually updating its testing protocols, AVLab provides valuable cybersecurity analysis to help both consumers and businesses make informed decisions about their digital security.

