Visibility of attacks in telemetry and incident response from the perspective of SOC (Security Operation Center)
Endpoint Detection and Response (EDR) and eXtended Detection and Response (XDR) are derived from the multi-layered endpoint protection developed over the years. Their main task is to monitor operating systems and applications in the cloud in real time. Properly implemented, they take threat hunting to a higher level, allowing to see indicators of compromise. For any company, this might mean having access to useful information from all endpoints which will certainly contribute to better protection of the entire network as well as employees against cyberattacks.
Using products of this class gives an overview of technical information from the entire infrastructure. In other words, observing telemetry from cyberattacks gives a broader picture of what has happened in the past, and what is currently happening on endpoints. As this test proves, thanks to correlation of incidents from operating systems, EDR-XDR software can provide significant value to large and small organizations with any level of technical skill. At the same time, we would like to point out that the implementation of this class of product needs to be a conscious strategy to protect against cyberattacks.
EDR and XDR – differences
EDR solutions usually focus solely on endpoint security, while XDR covers a wider range of system integration. Both solutions are designed to identify and respond to cyber threats, but XDR supports more data sources, among others, mobile devices, IoT sensors, Web 2.0 applications such as Google Workspace and Microsoft Office, network logs from edge devices, IDS and SIEM systems, etc. The final choice between EDR and XDR should depend on the needs and complexity of the organization’s IT environment, but at the same time boundaries between EDR and XDR already start to erase in some security categories.
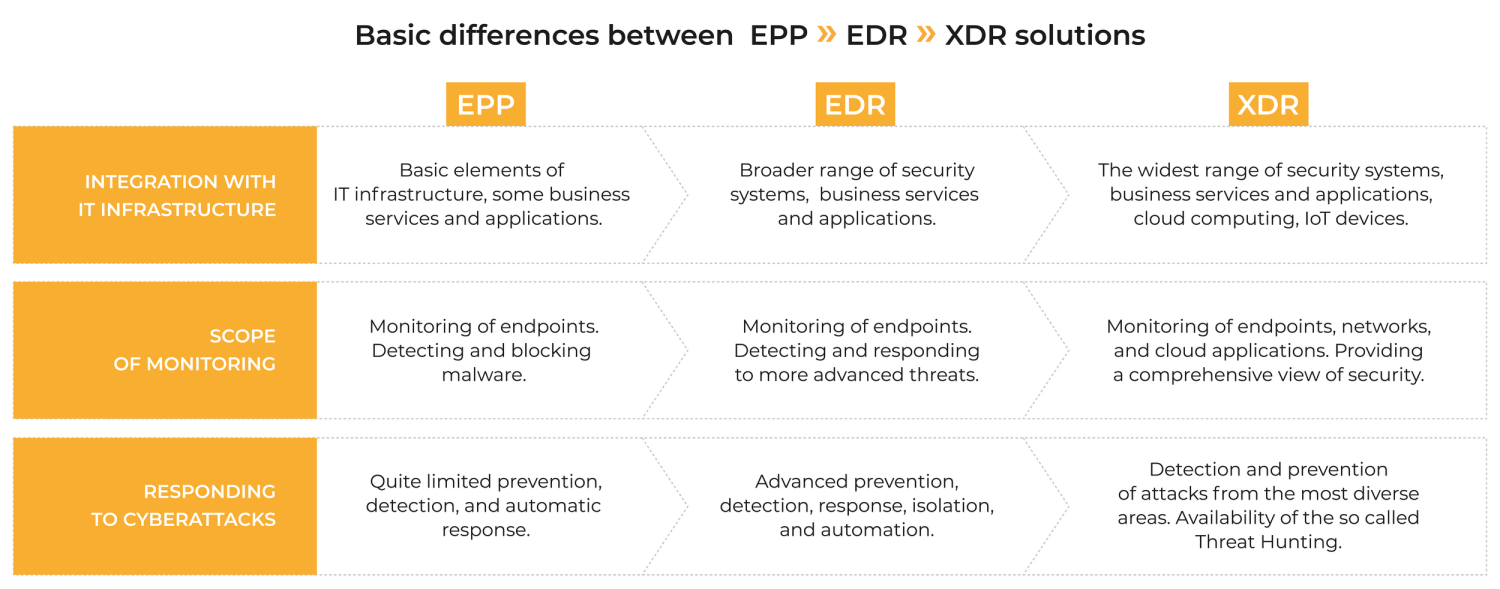
*The table above contains many simplifications. Not all features can be assigned to a single product category. For example, EPP solutions have evolved to EDR, and the differences between EDR and XDR are no longer as big as they used to be. The common core has been retained, i.e. an advanced protection of workstations against threats and cyberattacks, but it is EDR and XDR that can better correlate logs from different endpoints. In addition, they provide the most detailed data visibility and enable the so called Threat Hunting, effectively securing endpoints.
Why should you consider implementing EDR?
Thanks to EDR, IT security officers can monitor and analyze incidents that will correlate with system processes, files, network connections, registry key modifications, etc. Here, automation, as it is based on machine learning, allows to quickly identify suspicious or clearly malicious activity on devices. This is crucial in detecting advanced ATP attacks, including 0-day ones.
Solutions equipped with EDR offer very precise visibility of events from end devices. Some developers implement features known so far only from XDR. We are talking about the so-called Threat Hunting, thanks to which EDR works perfectly in the hands of malware analysts. It is also necessary to mention effective defense mechanisms, such as: isolating infected devices, searching for traces of intrusions, obtaining information about the course of the attack, revealing the initial attack vector, methods of spreading malware.

Why should you consider implementing XDR?
XDR combines the features of EPP and EDR. It uses telemetry from all endpoints, even from systems and applications in the cloud. It provides a comprehensive and holistic view of security of the entire infrastructure. With XDR, it is possible to identify attacks quickly and effectively. SOC teams can take appropriate remedial action just as quickly.
Products of this class make it easier to track not only suspicious activity at all levels of the IT infrastructure, but also seemingly trusted events, where the attacker’s malicious code may be among the so-called “system noise”. The solution takes security of the organization to a higher level by reducing the response time to threats and automatic repair of systems after a reported incident.
Telemetry and visibility of attacks – common features of EDR and XDR
We conducted an analysis of the EDR and XDR modules to justify the investment in a given product designed to protect systems against cyberattacks. As the Red Team, we simulated the actions of attackers who had gained access to the IT infrastructure. As Blue Team, we analyzed data from these attacks to assess the capabilities of the tested product to detect and respond to a threat.
Based on the data collected, we believe that the most important thing is that the product records traces of attacks in the administrator console. It does not matter if these events are processed automatically or manually by a team of qualified employees. The product must provide visibility into system events along with telemetry that allows to understand the context of the attack and capture the necessary technical details.
In this test, we did not test the effectiveness of protection against cyberattacks. Rather, we focused on ensuring that the solution guarantees visibility of incidents through attack telemetry. Lack of visibility of the incident or telemetry may mean that the product’s protection did not work or it detected a threat too late.
Testing solutions for business
The policy configuration for antivirus agents was usually default or included additional settings for more detailed telemetry. Importantly, we did not disable antivirus protection or any other features. Solutions that had to be assigned a predefined agent configuration after installation were configured with the most hardened settings possible to achieve detailed visibility into the attack chain and telemetry which was the goal of this test. At the request of the developers, we assigned the proposed settings.
- Emsisoft Enterprise Security + EDR: default settings. Website: emsisoft.com
- Eset Protect Elite + XDR: default settings + all rules for EDR enabled. Website: eset.com
- Microsoft Defender for Business + EDR: default settings. Website: microsoft.com
- Metras: default settings. Website: site.sa
- Xcitium Advanced + EDR: predefined policy 8.1. Website: xcitium.com
Configuration of victim system and agent
- To simulate the attacks, we used a virtual machine running Kali Linux as a Command and Control server with Metasploit software. In addition, the Atomic Red Team tool with predefined types of attacks, as well as the Caldera Framework and several of our own methods to deliver the malicious payload, and run on the operating system.
- Virtual machines with Windows 11 Pro with the agent installed of a given solution had full access to the Internet. We have applied the default Windows configuration.
- We have given up creating campaigns from start to finish. The so-called payload has been delivered using the described protocols without any social engineering because the type and purpose of the attack in the simulated scenario was known to the testers.

