In March 2022 took place already 17th edition of the Advanced In The Wild Malware Test in which we regularly verify software to protect devices. To check the effectiveness of detection and blocking malicious software we use so-called samples in the wild that can be found in many areas of the Internet a casual user may come across. In addition, to increase the number of samples in the test base, we need to capture them in greater numbers that is why honeypots are necessary.
Cycle of the Advanced In The Wild Malware Test is automated process, so it can run continuously 24 hours a day. In March we acquired 2050 unique malware samples. We verify all viruses before they are added to the test base, and in disputed cases, we discuss logs with developers.
In March 2022, we checked the following applications to protect desktops:
- Avast Free Antivirus
- Avira Antivirus Pro
- Comodo Advanced Endpoint Protection (for business)
- Comodo Internet Security
- Emsisoft Business Security (for business)
- F-Secure Total
- Malwarebytes Premium
- Microsoft Defender
- SecureAPlus Pro
- Webroot Antivirus
Unlike other testing laboratories, our tests are fully transparent, so we provide a complete list of virus samples and other technical details described in our methodology. Key information and test results are available at https://avlab.pl/en/recent-results.
Summary of March edition of the test
Notice the Level 3 of analysis because it shows protection against 0-day samples. But remember! Certain antiviruses of the next generation intentionally do not have protection in a browser (Level 1). Sometimes they do not have traditional protection based on signatures (Level 1 and Level 2), so without proper interpretation, such tests could favor other protection solutions. Not ours!
In the tests, we do not award negative or positive points for early blocking of threats. Security product must stop a threat in any way – provided by a developer. The final result is whether or not this has been achieved.
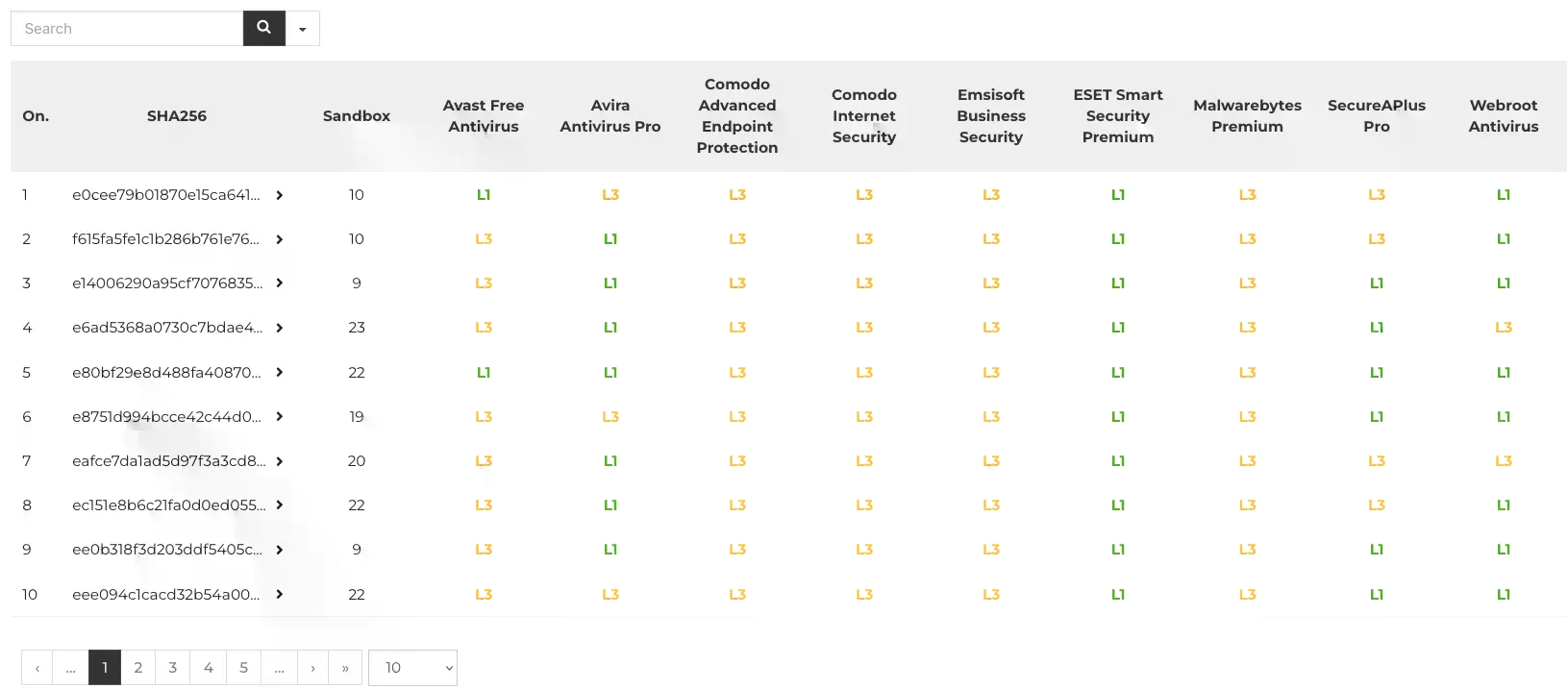
The so-called Level 1 shows early blocking of threats in a browser or on a hard drive.
If this fails, the next is Level 2: a virus is scanned by the antivirus based on signatures when moving from X to Y folder (obviously if such protection exists). In this study, there are many test cases when samples have not been verified by developers yet, so the next level of analysis is crucial.
Level 3 represents modern protection without any local signatures because a virus is run in the operating system. It is the most dangerous situation but needed because it shows true effectiveness of protection against 0-day threats.
Starting with May edition of the test, our methodology will be slightly changed in the layer of Windows. We will inform about the details in a few weeks.

