Ransomware threats aren’t a problem anymore. At least not as it used to be. Despite the popularity of cryptominers, bank trojans and mobile malware, the first place in all rankings is held by fileless malware, by which all the attacks begin. Other types of malware are estimated to be undetectable by signatures in 30% of all cases. These data concerning Q3 2018 were prepared by German network devices manufacturer, WatchGuard. This means that every third malicious file is a zero-day virus (it uses undiscovered software vulnerabilities or techniques to bypass security measures). The presented data gives food for thought, because we clearly see the rising trend of threats undetectable with traditional methods.
WatchGuard reveals that threat landscape nowadays is totally different from the one that was present two years ago. However, part of sociotechnic attacks is still focused on extorting money using cryptography techniques. On the other hand, Check Point shows detailed statistics concerning threats with focus on ransomware attacks:
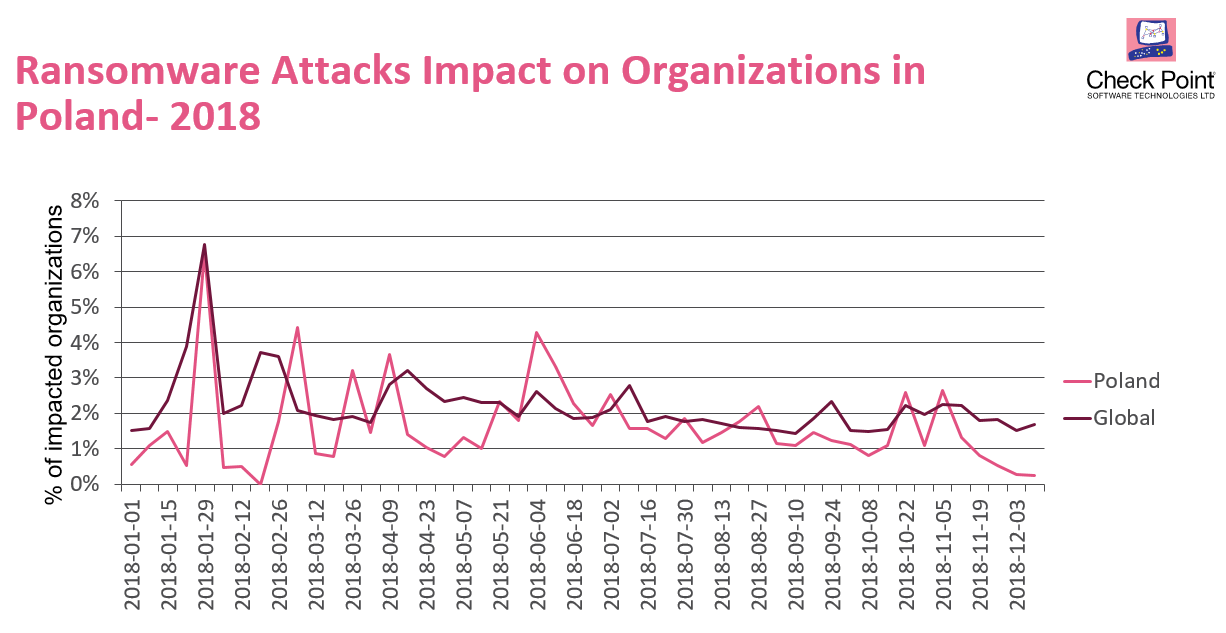
The most serious encryption attacks were conducted in 2017. The malware was spread all over Europe using previously unprecedented vector. Ethernelblue and Double Pulsar exploits, using SMB protocol vulnerability, were stolen from NSA and caused global chaos induced by, ironically, US secret services. Hacking tools used for gaining access to civilian computers were the main reason behind huge outbreak of low-quality lowdroppers and downloaders. Mass-produced malware samples caused percentage drop in cryptographic attacks. However, we still need to keep an eye on ransomware attacks which will not allow to be easily forgotten. Couple of weeks ago we observed increased activity of GandCrab ransomware, also in Poland.
Can encrypting malware harm files protected by ZoneAlarm Anti-Ransomware? We have checked that at the producer’s request.
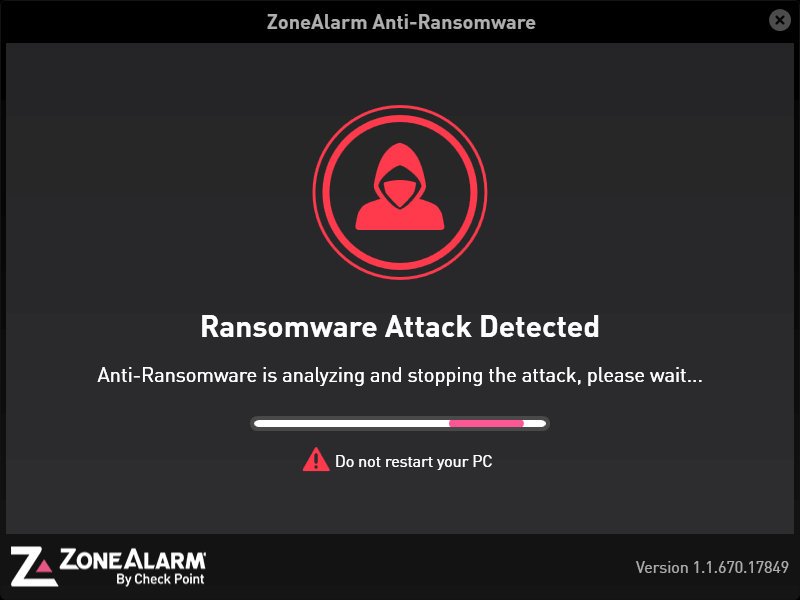
Check Point ZoneAlarm Anti-Ransomware – the basics
It is the first seconds after initializing a fake invoice or a notification of postal delivery that matter the most. This is when ransomware starts searching and encrypting the files – usually with AES-256 or AES-128-CBC algorithm. Then, on the server controlled by the attacker, public and private keys are generated by RSA algorithm. (usually RSA-2048 or a stronger one). This kind of public key is transferred onto the victim’s computer. There are also ransomware samples that already have a public key embedded in the code. Ransomware uses the public key to encrypt the earlier AES-256 key which was used to encrypt documents, movies, databases and computer games files.
The issue of factorisation has been an insanely tricky riddle for modern computers – finding divisors of a gigantic prime number such as 2^2048 generated during the creation of public and private key. This process would take millions of years for home computers. Thus, an express solution to such math problem is impossible (finding two numbers which product yields said gigantic prime number). Should anyone pull it off, they could be rewarded with 1 000 000 USD prize for solving one of the major mysteries of the millenium which are the prime numbers. This is why, in terms of cryptography, huge prime numbers bring an advantage to the offenders. A movie titled “The curse of Prime Numbers” provides a great insight into the problem. The author explains why the efforts taken to break the RSA-2048 are doomed to fail.
Within a reasonable time, and without paying the ransom, it’s impossible to neither calculate the private key nor decipher the files, even for quantum computer unless:
1. Forensic bodies such as European Cyber Crime Centre – EC3 or Europol, together, take control over the server that hosts the halves of RSA keys or lead to the offender’s incarceration. The prosecutor usually offers shorter sentence if the suspect is cooperative.
2. The encryption algorithm used in the malware’s code should not be implemented correctly; only then the chance for successful development of deciphering tool that uses the vulnerabilities in algorithm implementation may arise.
3. Encryption algorithm used in the malware’s code is not using RSA (asymmetric cryptography), which, nowadays, happens extremely rarely..
Providing that one of the beforementioned conditions is met, only then it is possible to formulate a deciphering tool.
The steps of encrypting files by ransomware usually go as follows:
- The user receives an e-mail with a link or an attachment.
- The victim is redirected to a website with exploit kit – a tool for automatic computer infection (or the malicious document is immediately opened). Then, the malware communicates with the server controlled by the threat actor.
- Ransomware reproduces itself and runs the binary file. Very often it runs the vssadmin.exe process with a parameter in control of deleting Windows’ backup copies. For example:
"C:WindowsSYsWOW64cmd.exe" /C "C:WindowsSysnativevssadmin.exe" Delete Shadows /All /Quiet
- The files are encrypted with randomly-generated AES key. Then, the key is subject to additional encryption by the public RSA key. The private key, which is essential in decrypting, is owned by the cyber-criminal and may be revealed only after the victim pays the ransom.
- The malware downloads a ransom demand note and displays the alert on the desktop.
Although no statistics have been made, we know that paying the ransom (usually) allows the victim to decrypt the files. However, there are cases where the victim is unable to recover their files after having paid the ransom (due to the offender’s inability to identify the victim). Antivirus software is more and more often removing ransomware, which deprives victim of a chance to decrypt the files. What’s more, after encrypting files attack is not necessarily finished, because ransomware can load additional malware and steal private data, intellectual property and login credentials. Victims have to be alert to dishonest companies that claim to be able to decrypt files, while they really pay ransomware creators and then charge victim with cost with extra large margin.
Ransomware is an extremely dangerous type of malware because the data loss usually has gruesome effects
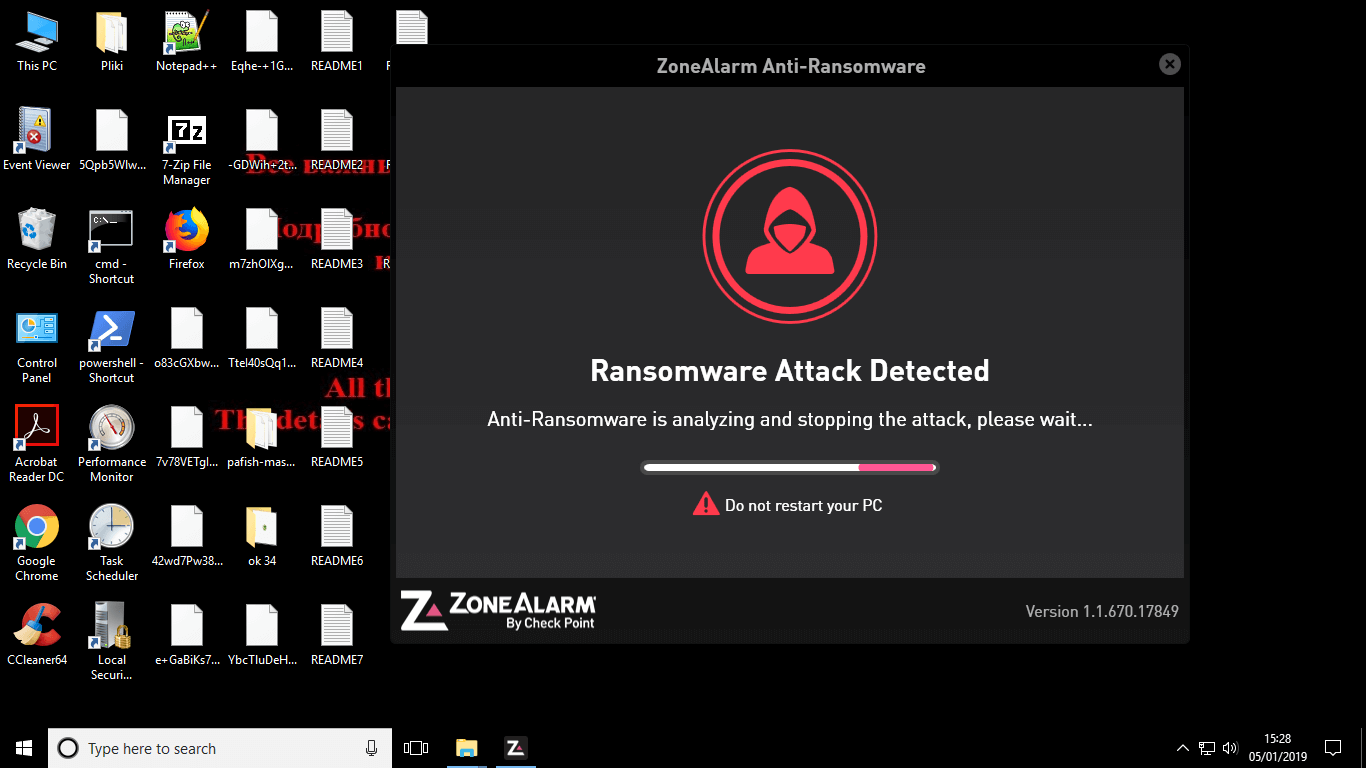
Bringing the files back to the original state takes just a moment. Plus, it doesn’t require us to have a back-up copy of the files. ZoneAlarm takes care of it during the encryption.
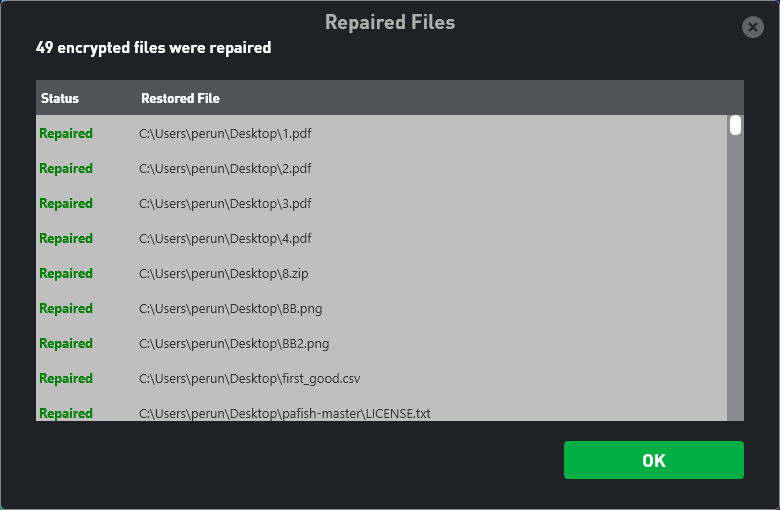
We’re done. ZoneAlarm Anti-Ransomware finished doing the job. All the encrypted files have been brought back and saved intact in the folders they were stored in originally. ZoneAlarm Anti-Ransomware brings Check Point’s experience ZoneAlarm Anti-Ransomware is developed by Check Point, that’s why it employs Threat Emulation technology of Sandblast products. We have tested the said protection technology a couple of weeks ago (Check Point’s Sand Blast for Browser solution was the only one to block all the malware samples). Complete set of Threat Emulation technology solutions is available in advanced firewalls or as a SaaS service under the name Check Point Sandblast.
Summary
ZoneAlarm Anti-Ransomware is a software that does not download the definitions of the viruses because it does not need them. It doesn’t protect the files from encryption like traditional antivirus tools do. Instead, it employs the leading technology Threat Emulation which permanently works real-time, monitoring and shielding computer from any symptoms of ransomware attack. Advanced behavioral analysis is capable of immediate detection of encryption attack and files’ restoration.
Monthly fee for ZoneAlarm Anti-Ransomware is just about 7 PLN a month. It can’t be purchased in Poland directly, however, one can buy the license with a card or using PayPal.
ZoneAlarm Anti-Ransomware is a very good anti-ransomware tool. It can be installed on both personal and business computers. This is why we issue AVLab recommendation, with one reservation. The programme protects the computer exclusively from encryption attacks, that’s why it should be used along with another tool for Windows system protection.
In a full security package ZoneAlarm Extreme Security there is even more necessary components which can detect contemporary zero-day threats and attacks. Complete list of ZoneAlarm products is available on https://www.zonealarm.com.

