These conclusions are meant to reward those developers whose security software in the year 2020 were involved in tests performed by AVLab. We want entrepreneurs, companies, and individual users to be able to choose only good solutions to protect devices and data. This is why the “Advanced In The Wild Test” is characterized by the fact that it is not one-time comparison that nobody will remember after a few months.
Throughout the year developers update their software few or even several dozen times, improving product, fixing errors, and adding new features. Thanks to such extensive tests, it is possible to verify the protection effectiveness in the long term. This is important now when the remote work has become something normal for non-technical users of state institutions, students, and also private sector employees. For these reason, selecting a solution of the year 2020 is a good opportunity to try out the best antivirus applications. As always, we encourage you to analyze test results of various companies (not only ours). A comprehensive look at a product can help you make the right decision.
Cyber threats in the 2020
In January 2020 nobody predicted in what direction the economy will be heading. Political decisions implied by a global pandemic have turned the world upside down. To a large extent employees have been forced to move to remote work. Companies have noticed that they can save, but it is just one side of the coin. In one of the study, the long-term impact of isolation on a company and employees has been checked[1]. People who have been sent home for the first time, do not have developed good practices of maintaining the around-the-clock balance between employee duties and their personal life. Due to a compulsory isolation, this was some kind of a social experiment. It is difficult to freely exchange thoughts over the wire. It is even harder to consult spontaneously. And while the transition to video conferencing has fulfilled its role (to some extent), for many people participating in online meetings has became exhausting in the long run. Let’s just hope that in these difficult times when cybercriminals take their toll, no one forgets about protection because statistics remain intact.
There was a noticeable increase in attacks via email during the pandemic period from March to December 2020. Cybercriminals were sending many more messages with malicious content than last year during the same period. A developer of the oldest Polish antivirus, MKS-VIR.pl, recorded an increase in zero-day threats[2]. Fortinet’s statistics reveal a reflection of media hype around cyberattacks[3]: 60% of companies have experienced an increase in IT security breach attempts when moving to remote work, and 34% have reported real attacks on their networks. It has got to the point that they have started to detect even 600 new phishing threats every single day, while a number of viruses increased in March 2020 by 131% compared to March 2019. Anyway, phishing is only the tip of the iceberg.
Subsequently, there are ransomware, trojans, remote access trojans, MaaS (Malware-as-a-Service) intended for novice cybercriminals. Interestingly, we can see decrease in the number of botnets[4]: in January – 66%, in February – 65%, in March – 44% (year on year). Attacks on mobile devices also decreased: in February – 10%, and in December – 5%. Number of potentially unwanted applications has decreased by 2%, and Adware by 18%. Avira has recorded increase in number of malicious attachments prepared in Word, Excel, and PowerPoint by 4%. There are 38% more exploits with each successive operating system versions[5]. This means that cybercriminals react to the crisis, adjusting strategy attack strategies to it.
Despite a global decrease in attacks not associated with the topic of COVID, hackers still harass corporate and administrative networks. The Trickbot and Emotet trojans responsible for sudden increase in ransomware attacks on hospitals and health care are the most commonly used software by cybercriminals[6]. Emotet is the most active threat in recent weeks, and it remains the most popular malicious software with global impact on 12% of organizations. It is followed by Trickbot and Hiddad that have influenced 4% of organizations worldwide. In Poland, Emotet mentioned earlier is the most frequently detected malware (8,1% of infections). According to the Trend Micro company, creators of Emotet are not out of the competition yet because this trojan is still the worst nightmare for individual users, and small and medium-sized companies.
[1] https://www.biznesinfo.pl/praca-zdalna-091120-pt-powiklania-badanie
[2] Data have been provided by the developer.
[3] https://avlab.pl/fortinet-prezentuje-globalny-raport-o-cyberbezpieczenstwie-pracy-zdalnej-2020/
[4,6] Statistics has been provided by Check Point.
[5] https://www.avira.com/en/blog/malware-threat-report-q3-2020-statistics-and-trends
[7] https://www.facebook.com/TrendMicro/photos/a.443467627960/10158165780147961/?type=3
The Advanced In The Malware Tests. What exactly is it?
These are studies that examine protection in real time whose task is to verify the effectiveness of blocking threats over a long period of time. We recreate user behavior when he uses the Internet and a browser. Also due to the malicious software behavior, the test is the most beneficial for developers because it indicates the type of technology that has contributed to block a threat (Level 1, Level 2, Level 3; more information in the methodology). Therefore, the test is kind of confirmation that technologies to protect against malicious software actually work.
Now, let’s get to the summary of six editions of the Advanced In The Wild Malware Test in which a total of 6713 samples of malware have been used. Some samples were unknown on the day of the test for certain antivirus programs tested, corresponding to a zero-day threat.
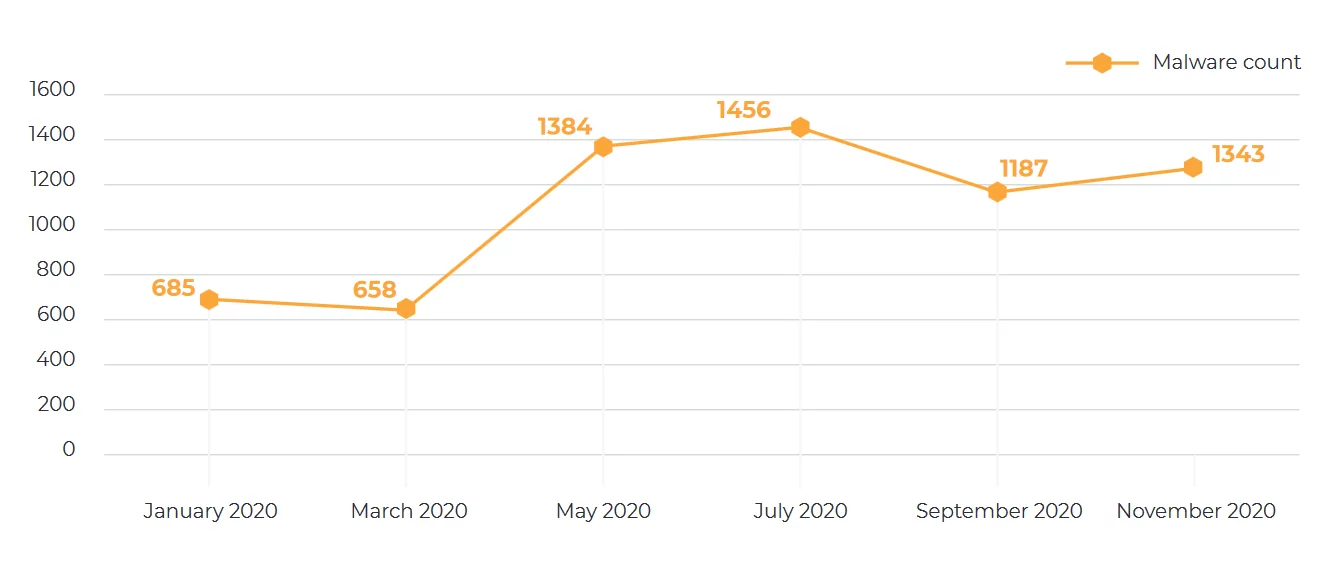
The summary of the Advanced In The Wild Malware Test
A product had to meet certain conditions in order to win the award of the year 2020 which is a special certificate:
- It had to participate in all tests in the year 2020 under edition of the Advanced In The Wild Malware Test.
- I had to block all samples in every edition of the test.
A solution could not get a unique certificate if:
- A product has failed to block at least one sample in any edition of the test. In addition, a product that has participated in all tests and blocked 100% of threats, gets better final assessment than a product that has participated only once in the tests.
- A product has not participated in all editions of the test. Certain developers declare willingness to participate to check protection just once in order to obtain a certificate. Having in mind the long-term nature of the tests, we must take into account both groups by granting appropriate priority of the evaluation.
We carried out 6 editions of the test in the year 2020. Every study was carried out with one month interval after the previous. For example, starting from January: we sent a feedback to developers in February, and then we published results. We started the next edition in March. Likewise, in the further months. During the whole year 2020, we used 6713 samples of unique malware in the tests. This means that throughout the year there have not been cases of testing the same malware sample.

