The July edition of the Advanced In The Wild Malware Test for the 14th time verifies security effectiveness of software from developers very well known in the cybersecurity industry. In our study that is complaint with MITRE procedures and techniques, we have analyzed 7 security solutions that protect wide range of devices. The test lasting uninterruptedly for the whole month, 24 hours a day, was possible to carry out thanks to a programmed system that performs tedious calculations and actions in the Windows system, automating the entire test procedure (aggregating and analyzing logs, giving a final verdict). The design and operation of this system are described in this article and in the methodology.
In the test, we considered these program versions that have been suggested by developers. Here is the full list of tested solutions (in alphabetical order):
- Avast Free Antivirus
- Avira Antivirus Pro
- Comodo Advanced Endpoint Protection
- Comodo Internet Security
- Emsisoft Business Security
- SecureAPlus Pro
- Webroot Antivirus
Levels of blocking malicious software samples
We share checksums of malicious software for researchers and security enthusiasts by dividing them into protection technologies that have contributed to detect and stop a threat. According to independent experts, this type of innovative approach of comparing security will contribute to better understand differences between products available on the market.
Each malware sample blocked by tested protection solution has been divided into few levels:
- Level 1 (L1): The browser level, i.e., a virus has been stopped before or after it has been downloaded onto a hard drive.
- Level 2 (L2): The system level, i.e., a virus has been downloaded, but it has not been allowed to run.
- Level 3 (L3): The analysis level, i.e., a virus has been run and blocked by a tested product.
- Failure (F): The failure, i.e., a virus has not been blocked and it has infected a system.
The products and Windows 10 settings: daily test cycle
Tests are carried out in Windows 10 Pro x64. The user account control (UAC) is disabled because the purpose of the tests is to check the protection effectiveness of a product against malware, and not a reaction of the testing system to Windows messages. Other Windows settings remain unchanged.
The Windows 10 system contains installed the following software: office suite, document browser, email client, and other tools and files that give the impression of a normal working environment.
Automatic updates of the Windows 10 system are disabled in each month of the tests. Due to the possibility of a malfunction, Windows 10 is updated every few weeks under close supervision.
Security products are updated one time within a day. Before tests are run, virus databases and protection product files are updated. This means that the latest versions of protection products are tested every day. All antivirus applications had access to the Internet during the tests.
VirusTotal vs real working environment
We use real working environments of Windows 10 in a graphic mode, that is why the results of individual samples may differ from those presented by the VirusTotal service. We point that out because inquisitive users may compare our tests with the scan results on the VirusTotal website. It turns out that differences between real products installed on Windows 10 and scan engines on VirusTotal are significant.
Malicious software
In July, we used 1311 malware samples for the test, consisting of, among others, banking trojans, ransomware, backdoors, downloaders, and macro viruses. In the contrast to well-known testing institutions, our tests are much more transparent – we share to the public the full list of harmful software samples.
The latest results of blocking each sample are available at https://avlab.pl/en/recent-results/ in a table:
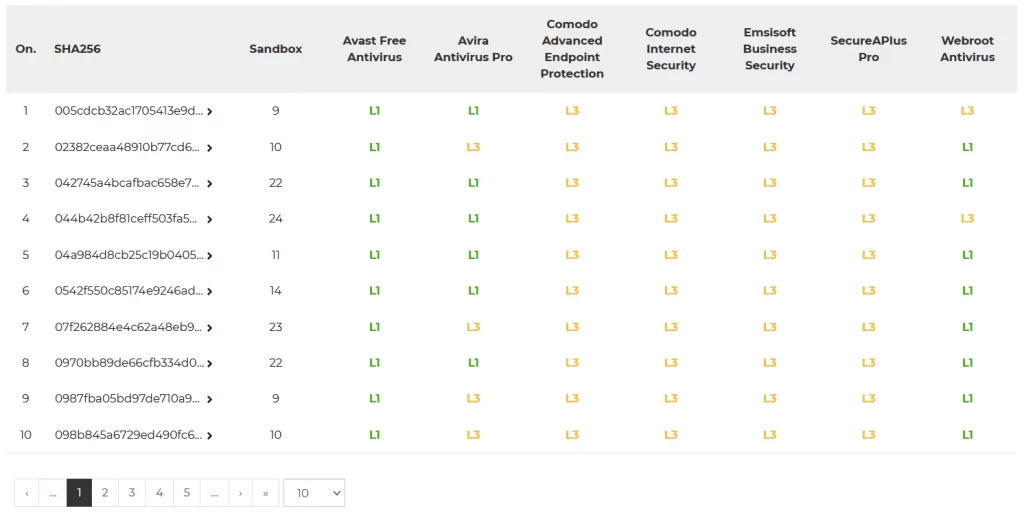
Summary of the July edition of the test
The results of our security test are not surprising at all. All developers who participated in the July edition blocked 100% of malware samples that have been caught be honeypots. It is worth noting the approach to protection that is specific to each producer. Some companies focus on developing technologies that block threats at an early stage, while other focus on modules that become active only when malware tries to run from a hard drive. In addition, no product relies solely on a single layer of protection that stops all kinds of threats. Instead, a user is equipped with a set of modules, tools, and technologies that work together to create a barrier ready for each type of malicious software.
Regardless of the direction to be taken by a developer, the goal should always be the same – the highest possible level of protection.

